Data Protection Analysis in Cloud Computing
Full text
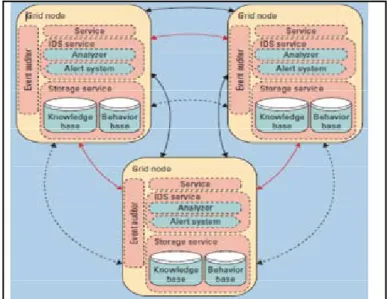
Figure

Related documents
An introduction form for a given type gives us a way of constructing elements of this type. An elimination form for a type gives us a way of using elements of
Measuring the mechanical properties of spinal cord tissue: Spinal cord tissue has been measured using a range of ex vivo and in-situ techniques, and it has been found to
Older age, more pre-war, war and post-war traumatic events; higher levels of posttraumatic stress, being unemployed and living in collective accom- modation were all associated with
In any business, customer is king of market. The main customers of „Divya Bhaskar‟ are its Advertisers. They respect their customers as king. They get their profit from
Cultural intelligence and cultural experience are discussed as separate matters, though later on the literature review discusses how they are interconnected. The objective of the
The sum of the actual instructional hours that a pupil was enrolled in and attending at the high school and at an eligible postsecondary institution plus the actual travel time
y E.ON opts for the integration of Denmark and Sweden into the single European gas market since we regard this as the most probable solution granting competitive gas and
In the following pages, you'll find 137 real world Instagram Ads that our team picked as the best among thousands to inspire you and help you test new approaches. Remember: