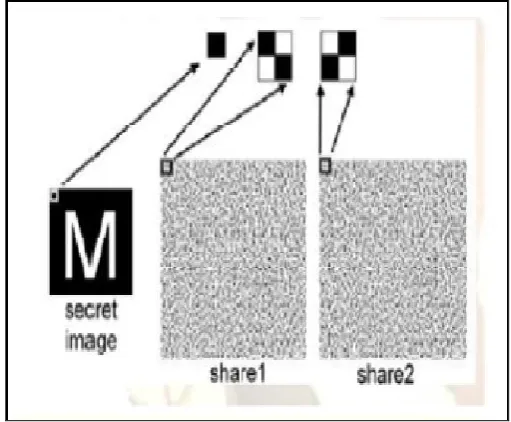
Image Password Based Security System
Full text
Figure
Related documents
We review the tasks reported in the published literature, spell out the language processes assessed by each task, list the cortical and subcortical regions whose
It was decided that with the presence of such significant red flag signs that she should undergo advanced imaging, in this case an MRI, that revealed an underlying malignancy, which
As a consequence in the past fi scal year GEA Group’s order intake fell by 1.1 percent year- on-year (excluding the Thermal Engineering Division, which is characterized by large
We wanted an integrated system that can support our global operations while providing our business executives with the insight they need in order to make fast, smart and
However, the presence of smaller and denser stomata shown to be associated with diploids (Li et al) has been hypothesized to be a beneficial combination for drought
ERBB2 amplification, germline BRCA1/2 mutations, PIK3CA mutations were classified tier of evidence IA based on large randomized trials showing antitumor activity of
The expression of surrogate tumor Ags and a convenient method for moni- toring the tumor progression and for detection and ana- lysis of TAA-specific T-cell responses, as illustrated
On the tourist data menu page the admin chooses the added function to display the form for adding tour package data.. Admin is asked to fill out a form for additional tour