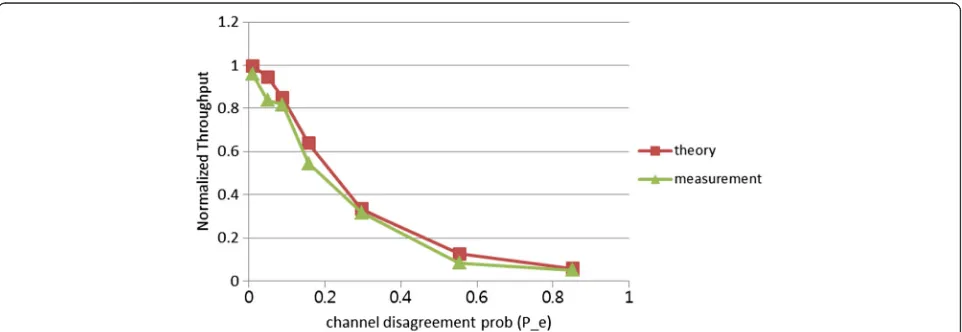
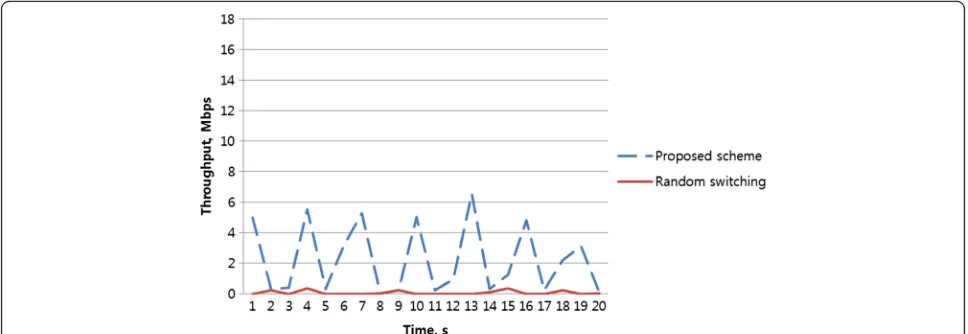
Channel hopping scheme to mitigate jamming attacks in wireless LANs
Full text
Figure




Related documents
14 participants (n=20) reported that the scenarios had made them reflect on mentoring skills and how they could use scenarios to assist the students in linking theory to
I therefore wanted to explore how the notion of ‘woman centred care’ evolved and to explore what ‘woman centred care’ meant to both pregnant women and the
Furthermore, although the majority of leadership, work and activism within the area of ‘domestic violence’ is carried out by women, and despite the relative smallness of
Considering the evolution of GPU’s hardware architecture, the proposed frameworks cover through the transition of graphics-originated concepts for GPGPU programming
Cricket’s Regional Identities: the Development of Cricket and Identity in Yorkshire and
I apply autoimmunity in the context of hospitality in order to challenge the tendency towards an immunity of shutting down borders, stricter acceptance policies, economic
A cultural shift in the maternity services Prior to this research being undertaken, the participating women had located previous birthing experiences within a medical model
Much of the blame for political spin has been laid at the door of politicians and their politically-appointed so-called ‘spin doctors’, special advisers of whom the Director of