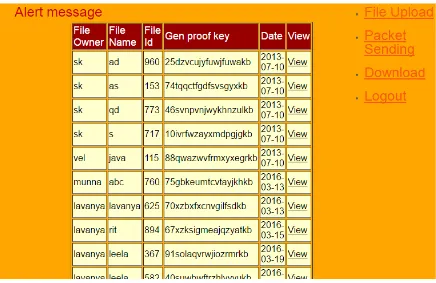
Secure User Data Using Encryption For Preserving Private Data In Cloud
Full text
Figure


Related documents
Using a spatial working memory task, Azuma and colleagues found lower activation in a parietal region in patients with 22q11 deletion syndrome compared with healthy controls,
This study investigated the fish diversity of Eko – Ende and Owalla reservoirs, which are within the Osun river system in South West, Nigeria with a view to
To handle user requests in a dialog program, you must assign function codes to the relevant screen and window elements in the Screen Painter and menu Painter, mark the element
The co-integration result shows that exchange rate, inflation rate and real gross domestic product like corporate tax have a long-run relationship with FDI.. Finally,
ZBDB uses columnar storage and massively parallel processing on a Graphics Processor to handle all of your data. ZBDB seamlessly distributes your data and queries over thousands
Effects of unconventional monetary policy (UMP) on disaggregated consumers’ inflation expectations in the euro area (EA)... Since 1999, the ECB has overseen the implementation of
to investigate prevalence and incidence of pressure ulcers upon arrival and at discharge from hospital, and to identify potential intrinsic and extrinsic risk factors for development
In the Daphni texts, however, I have not found any clear example of it, whereas I have found many places where the permeation of text through layers of papyrus has produced