A SURVEY ON DATA SECURITY IN CLOUD COMPUTING
Full text
Figure
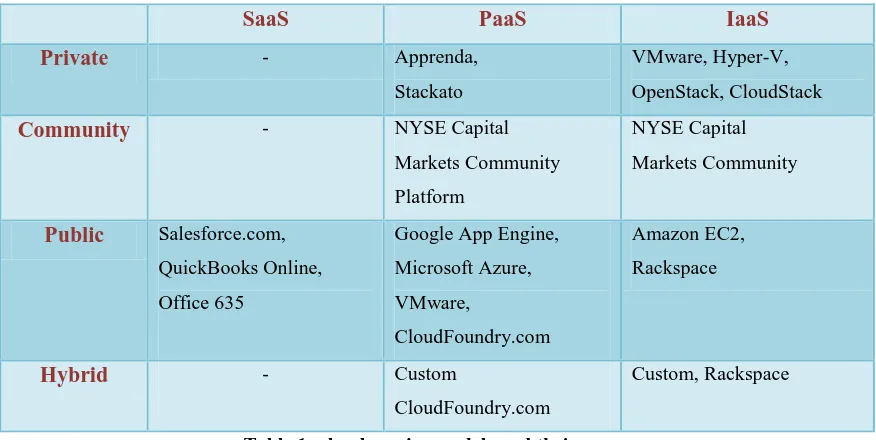
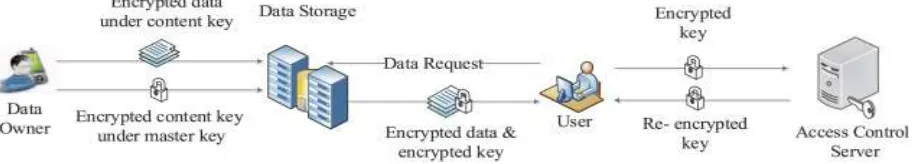
Related documents
The Service Provider shall at all times Indemnify and keep indemnified that Department against any claim on account of disability/death of any of its personnel caused while
To ascertain the different methods of analysis of a simply supported concrete bridge deck and the advances or improvement made to reduce several joints associated
In response to the director's inquiry regarding any special or advanced duties the beneficiary will perform, the petitioner emphasized that, during his tenure with
Table 3b shows that when SENTIMENT is positive, monthly returns are 0.32 percent higher on profitable than unprofitable firms and 0.45 percent higher on payers than nonpayers..
Abstract – The objective of this work was to verify the existence of a lethal locus in a eucalyptus hybrid population, and to quantify the segregation distortion in the
This paper presented an electric field integral equation that is immune from both low-frequency and dense discretization breakdown, does not require a search for global
Improving retention strategies for experienced nurses based upon the described influences on nurses’ decisions to leave patient care settings can effectively promote
Each Party shall accord national treatment to the goods of another Party in accordance with Article III of the General Agreement on Tariffs and Trade (GATT), including