Machine Learning approaches to Keystroke dynamics based authentication system with Enhanced Features
Full text
Figure

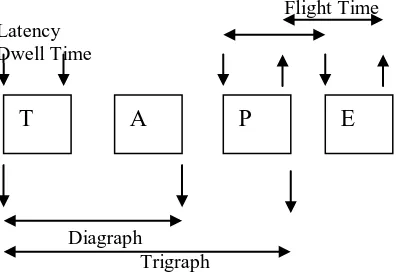

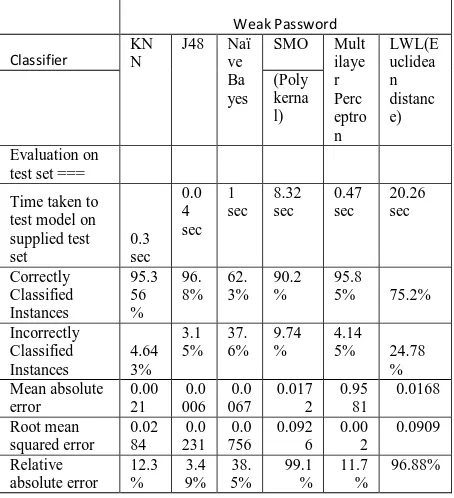
Related documents
Notation. If this condition.. holds we shall say that A has bounded relative units in the sense of Bade. The other definition, used more frequently, is stronger, insisting that
Moreover, we construct a crystallization Γ corresponding to the Heegaard diagram H and show that at least one among the Heegaard diagrams associated with Γ is transformed into
214] in his book, Dreams of a Final Theory , “In contrast, the strings that concern us here are truly fundamental and keep vibrating forever; they are not composed of atom or
Hyperbolic equations, duality theory, optimal control, convex cost function, positive control, distributed control systems.. 2000 Mathematics
Some related fixed points theorems for set valued mappings on two complete and compact metric spaces are proved.. Keywords
Ikehata, On global solutions and energy decay for the wave equations of Kirchhoff type with nonlinear damping terms , J. Yamada, On global solutions of some degenerate quasilinear
To achieve this result, we consider the Sasaki-Finsler metric G on T M and prove that the linear connection of the Cartan connection on F m is just the projection of the
The result (4.2) is very reasonable in the steady state where the population has died out because (4.2) means that the birth rate of susceptibles, a , is very small and much
