Exploitation of Server Log Files of User Behavior in Order to Inform Administrator
Full text
Figure
Related documents
your Policy Schedule, means that, where the Funeral Cover Benefit for a Life Insured is cancelled or lapses after a 5 year qualifying period, the NRMA Insurance Payment Promise
• Web-based log file analysis software designed to analyze Web server, streaming media server, FTP server, proxy server and firewall log files?. • Generates detailed and
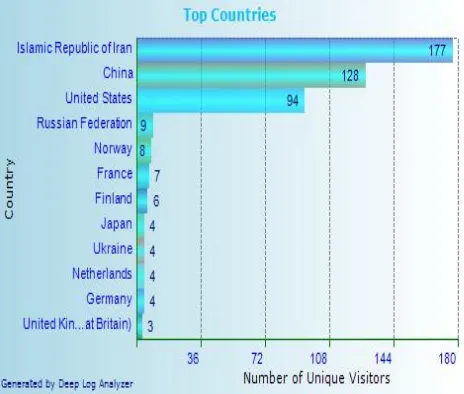
Analysis of this pertinent information will help companies to develop promotions that are more effective, internet accessibility, inter-company communication
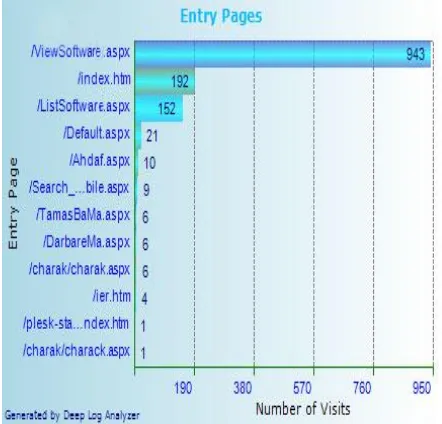
In this section, we would be able to identify the Hits statistics like Total Hits, Visitors Hits, Average Hits per Day, Average Hits per Visitor, etc., Page View Analysis like
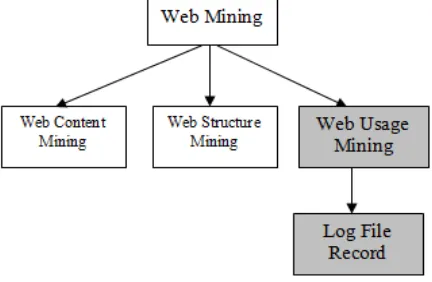
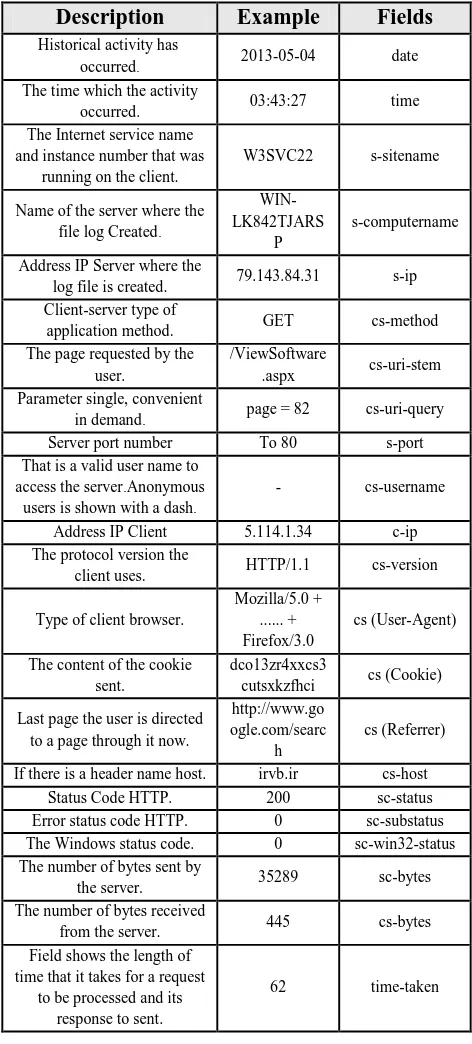
Web Server Logs Using Web Usage Mining Web Usage Mining process , W3C log file format Uses unstructured data Worked on. single log file
ANALYSIS OF WEB SERVER LOG FILES TO INCREASE THE EFFECTIVENESS OF THE WEBSITE USING WEB MINING TOOL..
There are four phasesinvolved in web usage mining: (1) Data Collection: users log data is collected from various sources like server side, client side, proxy
Web usage mining techniques have been widely used to discover interesting and frequent user navigation patterns from web server logs.. A novel approach for classifying