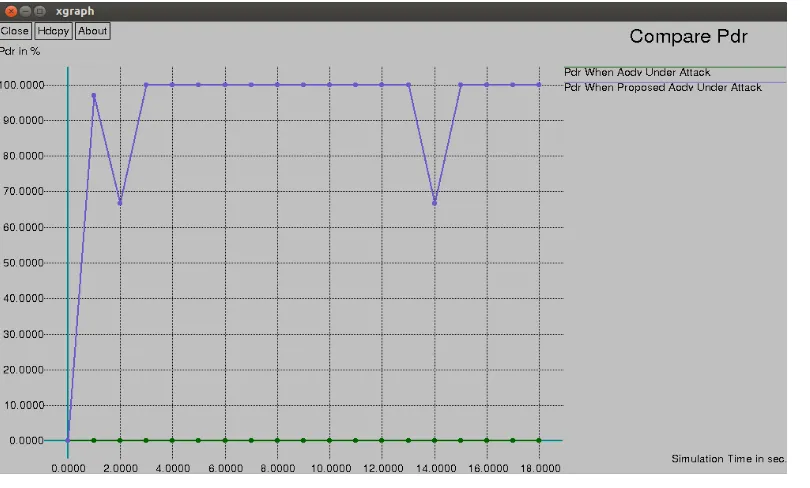
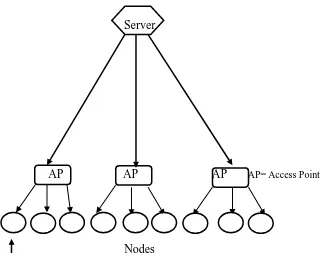
An Implementation of Secure Wireless Network for Avoiding Black hole Attack
Full text
Figure



Related documents
It is suggested that a possible association between the w+ and N + loci in the duplication and the homologous region of the X chromosome may be implicated in a n
Based on this technique we investigate the minimal effort for an adversary to obtain a failure in 3 cases: when he has access to a quantum computer, when he mounts a multi-target
Next, the article has the following structure: Section 2 presents an introduc- tion for the neutrosophic representation of information; Section 3 presents the metric for gray
Total carbohydrate content of all four alga was determined by Anthrone's method and the result depicted in table-3 shows that green alga Oedogonium has
The Basic-9 feature setTable I contains nine features that were used for experiments and Writeprints(Limited) feature set Table II contains features used for
Polychlorinated Biphenyls (PCBS) in Japanese Koi (CYPRINUS Polychlorinated Biphenyls (PCBS) in Japanese Koi (CYPRINUS CARPIO): Effect of Diet on Chemical Assimilation and Influence
In earlywood (upper panel, Fig. 3), the cell lumen area decreased with increasing cell wall area at an early stage of [C2mim][Cl] treatment.. After these initial changes in cell
Individual compounds of free fatty and resin acids and sterols were identified by comparing their gas chromato- graphic retention times and total ion detection mass spectra with