Secure Multicasting in Ad-Hoc Network
Full text
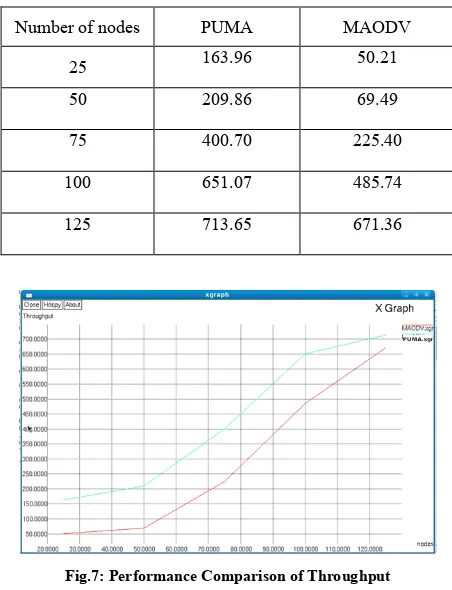
Figure
![Fig. 1a: Multicast announcement [2]](https://thumb-us.123doks.com/thumbv2/123dok_us/8741765.889802/4.612.43.570.380.691/fig-a-multicast-announcement.webp)
![Fig. 2: Dissemination of multicast[2]](https://thumb-us.123doks.com/thumbv2/123dok_us/8741765.889802/5.612.341.545.476.645/fig-dissemination-of-multicast.webp)
![Fig 3: Mesh creation in PUMA [2]](https://thumb-us.123doks.com/thumbv2/123dok_us/8741765.889802/6.612.341.545.133.333/fig-mesh-creation-in-puma.webp)
![Fig 4: Mesh structure of ODMRP [2]](https://thumb-us.123doks.com/thumbv2/123dok_us/8741765.889802/7.612.57.272.245.498/fig-mesh-structure-of-odmrp.webp)
Related documents
Doprinos tehnik prevzema prometnega signala na manjˇ sem oziroma veˇ cjem delu cestnega omreˇ zja Ljubljane podaja tabela 5.5, ki vkljuˇ cuje tudi podatke o povpreˇ cnem izboljˇ
Abstract :The purpose of this study is to determine the relationship between student perceptions and student attitudes towards natural science. The perceptions of
Despite the varying environmental and climatic conditions of the West African Sahel, we show that it is possible to increase the performance of the GR2M model simulations by
A simple model of the risk of securities in markets where capital flows freely is the international capi- tal asset pricing model, which states that the return of a security
of the Late Roman Fortification and belonged to the monument on the axis of the Stoa had at the left edge of its face an inscription consisting of one or two
TLS Traffic Light System TJS Traffic Junction Simpang SUMO Simulation of Urban Mobility PLC Programmable Logic Controller VIPs Video Imaging Processors SM Sequencing Method
In summary, the concepts of vocation and calling have many implications for the work of coaches, 385. applied sport psychologists, and career counsellors working with
Nessa perspectiva, cada história ilustrada e contada, independentemente da especificidade de seu tema, não está presa a nenhuma disciplina específica e, como o Programa