Secure Data Access Control with Cipher Text and It’s Outsourcing in Fog Computing
Full text
Figure

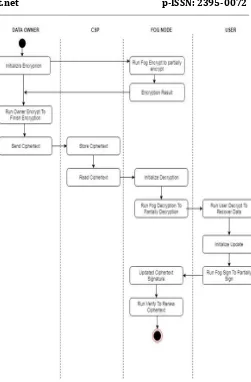
Related documents
This is an exploratory and descriptive study that sought to investigate the perception of certified fraud examiners (CFEs) on the suitability of using red flag behaviour
Each product required students to promote car safety through a compelling presentation of selected crash statistics and explanations of the physics laws that explain the results
Prof Shunji Matsuoka, a professor at Waseda University and also the general manager of the Campus Asia-EAUI programme, said: “We found that having a regional wide graduate
also exploring ways of managing the impact of academic talent void/academic staff attrition resulting from brain drain. The research explores the applicability of a profile
Description The create authen_enable method_list_name command creates a list of authentication methods for promoting users with normal level privileges to Administrator
Core Courses [27 sh] Credit (sh) PPUA 6201 The Twenty-First Century City: Urban Opportunities and Challenges in a Global Context 3 sh PPUA 6205 Research Design and Methodology
investigation. With respect to Citation No. 78559009, I have discussed above why I found no reason to modify any of the findings in the citation. There is no reason to diminish
Yes: Members Angelique Ashby, Steve Cohn, Darrell Fong, Robert King Fong, Kevin McCarty, Bonnie Pannell, Sandy Sheedy, Jay Schenirer and Mayor Kevin Johnson. Public