Internal Security in Metropolitan Area Network using Kerberos
Full text
Figure


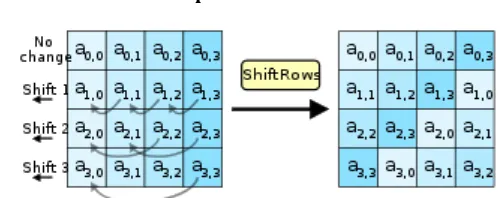
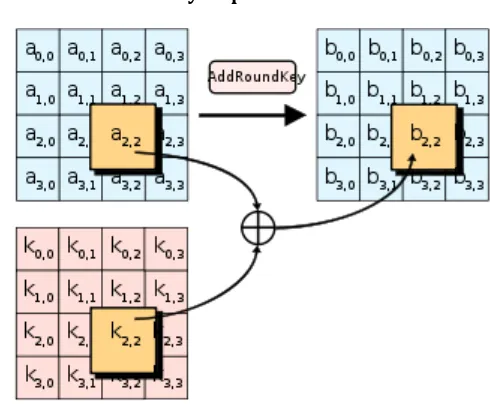
Related documents
BBC Worldwide, the main commercial arm and a wholly owned subsidiary of the BBC, had a strong business, but needed to turbo-charge its marketing capabilities if it was to
The strength of the relationship between earnings and future cash flows, and hence the precision of earnings-based price multiple valuation, should increase when one removes
To this aim, Tregs were enriched from the spleens of naïve mice and polyclonally stimulated in vitro in the presence of IL-2: in this context, we could detect an
Govaid mat leat interneahtas sáhttet skuvllat geavahit jus skuvllat čuvvot daid njuolggadusaid mat leat skuvllaid várás, ahte bidjá juohke gova báldii govvejeaddji namma og
Another WCRI study from July 2013 on physician dispensing in the state of Georgia (WCRI - WC-13- 21- Impact of Reform on Physician Dispensing and Prescription Prices in
• Northern Finance Association 2009 Conference (Presentation, Discussion) • Western Finance Association 2009 Meeting, San Diego (Presentation) • 1 st Financial Stability
• Chose a title that generates interest in the event, but which clearly articulates the purpose of the workshop. A well titled event helps librarians secure funding from
This means that even if two different frequencies within the near-infrared band were carefully chosen so that they have equally low absorption by the atmosphere, the range