The Simulation of Conveyor Control System Using the Virtual Commissioning and Virtual Reality
Full text
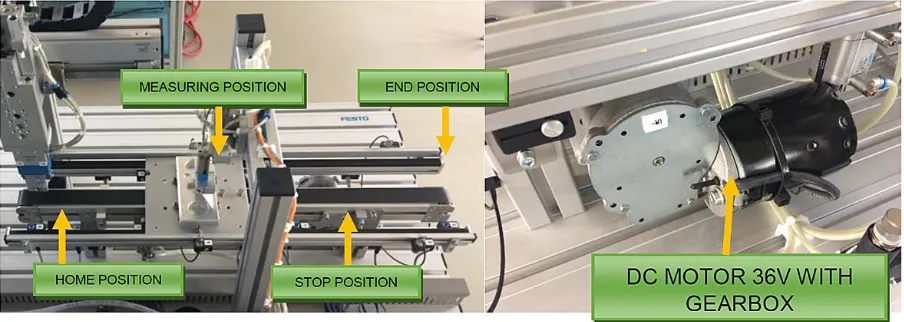
Figure



Related documents
The Institute of International Finance, (2013, p. 11) surveyed creditors in the Euro area and noted that high fixed costs of evaluating SME creditworthiness made it difficult for
The aims o f the present study w ere to generate m orphological and genetic data to support m anagem ent strategies for captive antelope populations. To achieve
Unlike the cyclic polygon problem, where the order of the sides does not matter, for the inscribed circle problem (our case) it does matter.. The solution is much easier than for
Species of the genus Bacillus are the most prevalent ones which exist in metal stress conditions in environment and are therefore used to remove heavy metals like chromium, lead,
Failure to Report Political Action Committee Contributions on a Timely Basis The Wright Committee failed to at least report at least twenty-four (24) contributions from political
According to the results and finding of this study which extracted from real data, and proposed literatures, it could be concluded that all these suggested characteristics such
PEF has been restructured under the Punjab Education Foundation Act- XII of 2004 for enhancement of education while encouraging the efforts of Private sector providing
services User data in Facebook Authentication OAuth 2.0 Authorization OAuth 2.0 Open Stream Applications Content Social graph Privacy policy Profile Identity Third-party site Client
