Network Access Control for Mobile Networks
Full text
Figure
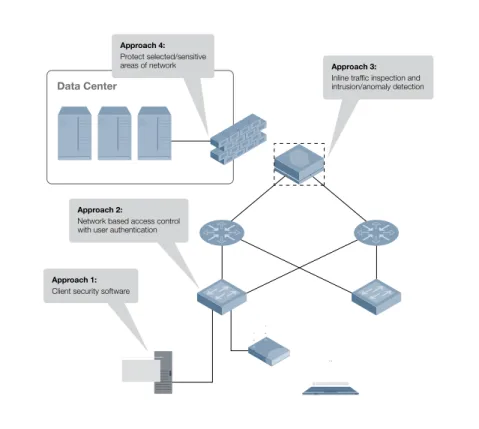
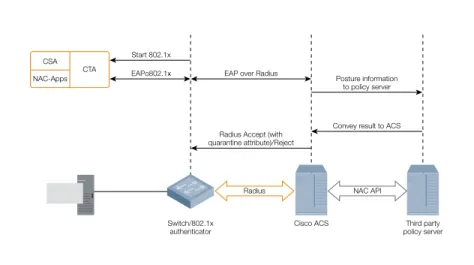
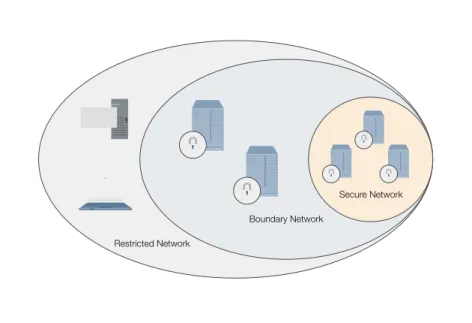
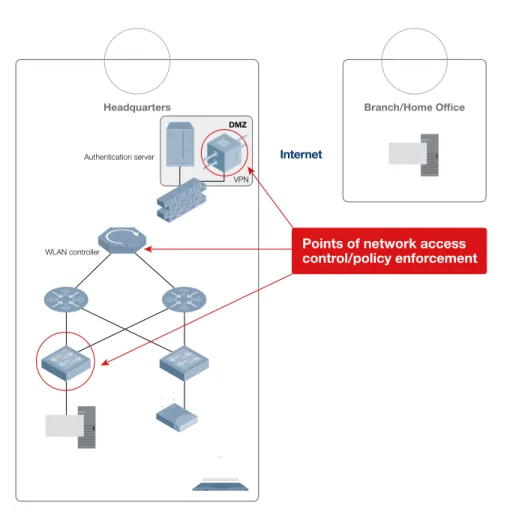
Related documents
The Symbolists wanted to become the mystics of art and, as stated in Part One, "it was Joséphin Péladan who’d proclaimed himself as the mentor of the movement." And so
- Install the Sophos NAC SQL database, see page 23 - Install the Sophos NAC application server, see page 23 - Configure the Sophos NAC application, see page 25 Create RADIUS
prevention/detection, firewalls, network admission control, remote access, secure VoIP networks, DDoS mitigation, connectivity, authentication solutions, web and content security,
Internal drivers of price volatility play a significant role: arbitrage practices, such as storage levels and trade flows, and market fundamentals, through consumption,
The isolation and access control delivered by the Rise Network Solution creates a secure private cloud for the customer and can contain multiple business IT solutions.. These
Automatically print cards and assign rights Link to CCTV and other systems Manage access based on membership packages... As ID card experts we can supply everything you
For cabinet level authentication, choose between fingerprint or RFID card (available Fall 2013). For end of row authentication, the user enters which cabinet door they are
It’s because we don’t operate a system that guarantees a trial lawyer will really know what he or she is doing before handling a tri- al.. Qualify as an attorney and you
