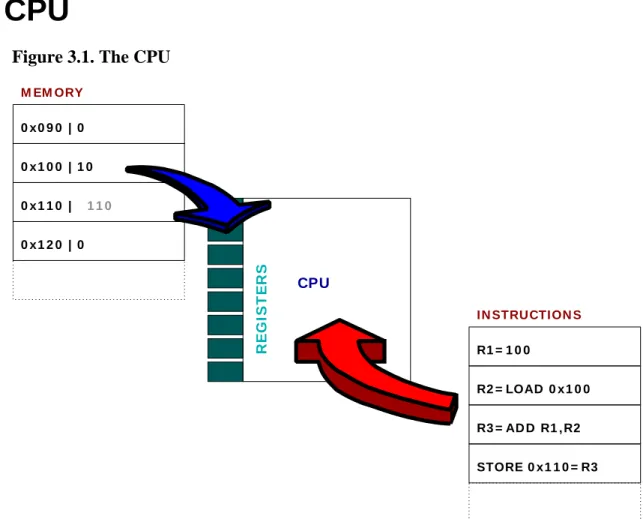
Computer Science from the Bottom Up. Ian Wienand
Full text
Figure




Outline
Related documents
So far researchers of this study know that there is no rich study which has been conducted yet covering the understanding of existing image of Sea beach
The paper is discussed for various techniques for sensor localization and various interpolation methods for variety of prediction methods used by various applications
The characterization of breathing sound was carried by Voice Activity Detection (VAD) algorithm, which is used to measure the energy of the acoustic respiratory signal during
Field experiments were conducted at Ebonyi State University Research Farm during 2009 and 2010 farming seasons to evaluate the effect of intercropping maize with
diagnosis of heart disease in children. : The role of the pulmonary vascular. bed in congenital heart disease.. natal structural changes in intrapulmon- ary arteries and arterioles.
Results suggest that the probability of under-educated employment is higher among low skilled recent migrants and that the over-education risk is higher among high skilled
In Step 2 we will look more closely at the links between thoughts, feelings and behaviours, particularly when we feel Anxious, Depressed and Angry. We will also start to learn
During the critical Encoding/Maintenance period, activity on trials with the highest level of accuracy (3 or 4 correct) is higher than trials with lower levels of accuracy.


![Figure 2.2. Types \0helloint achar cint b[2]char *h = "hello" 1 b y t e 4 b y t e s 6 b y t e s 2 x 4 b y t e s b[1] | *(b+1)b[0] | *b Sy st e m M e m or y](https://thumb-us.123doks.com/thumbv2/123dok_us/8432214.2243341/32.918.176.763.134.835/figure-types-helloint-achar-cint-char-hello-sy.webp)