Applying the multi threat framework of stereotype threat in the context of digital gaming
Full text
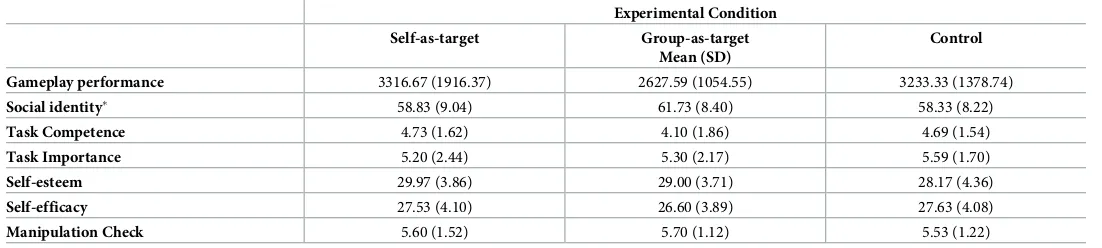
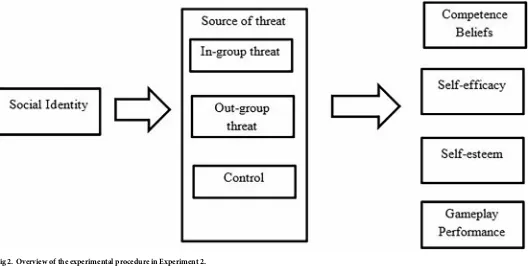
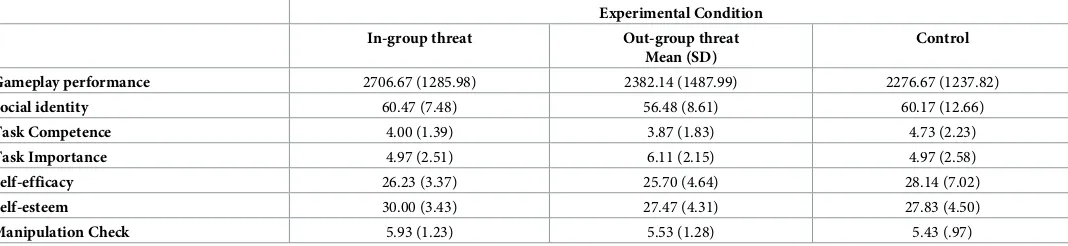
Figure

Related documents
Among indoor location techniques, those based in the Received Signal Strength (RSS) are of particular interest since they require neither the installation of extra infra-structure
In the ASHRAE Position Document on Filtration and Air Cleaning it’s stated that “even though the ozone is an unintentional by-product of operation, it may represent a net negative
We employed Lunapark-knockout U2OS cells (generated by CRISPR-Cas9 technology) transduced with lenti- viruses expressing physiological levels of either HA-tagged wild- type Lunapark
Hybrid automata are suited to express realtime behavior and VSE-II is suited to formally develop industrial sized systems.. Exploiting the advantages of both formalisms
Research highlights : This application has been designed to make it possible for any stakeholder to easily estimate standing vol- ume, biomass, and carbon content in maritime
Bevilacqua 1939, 50–56, who suggested that Timocles wrote two plays on the same topic, a satyr play with the title Icarian Satyrs and a comedy with the title Icarians; Sutton
Indeed, measurements in tokamaks sug- gest that electrostatic fluctuations may induce a significant fraction of the particle and energy losses.’ In addition,
ELIA will introduce a SDR from DSO-grid product applying no correction of BRP-perimeter in case of activation. According to CREG, Emergency gensets and CHP are not considered