A near optimal source location privacy scheme for wireless sensor networks
Full text
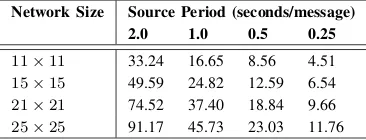
Figure



Related documents
Observations of high latitude geomagnetic field fluctuations during St Patrick?s Day storm Swarm and SuperDARN measurements De Michelis et al Earth, Planets and Space (2016) 68 105 DOI
Our empirical results suggest that equalization grants provide provincial governments an incentive to raise their business and personal income tax rates.. We also find that
Although it gives a symmetrical treatment to repos and reverse repos for transactions with banks, other financial institutions receive an asymmetrical treatment in the < 6
I aimed to address questions such as how the adaptation to environmental temperature is accomplished on the level of enzymes, and how the altered temperature
Further work with biological nutrient removal in a sequencing batch moving bed biofilm reactor (SBMBBR) should address design of a full scale process and also a comparison between
This thesis challenges the view of many historians that the natural law and natural rights tradition, while flourishing in the Enlightenment period, disappeared in nineteenth-
Autonomous Infrastructure, Management and Security (AIMS 2010) , Springer, ser. "Justifying a Policy Based
The results obtained show that the probability value of 0,000 is below the error level of 0.05, the decision is that Ho is rejected and Ha is accepted so it can be concluded that