Scheme for Secure Communication via Information Hiding Based on Key Exchange and Decomposition Protocols
Full text
Figure
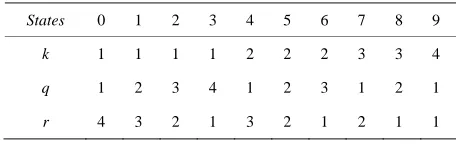
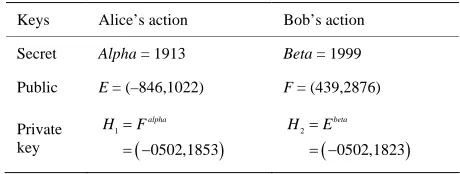
Related documents
In such a case, except when population sizes are extremely small, selection on variance is not expected to be sufficiently strong to favor the genotype with lower growth rate when
In our study some of sleep disturbances appeared associ- ated to semen quality; in particular lying awake most of the night were associated to lower motility and difficulty
Water hazard class 2 (German Regulation) (Self-assessment): hazardous for water Do not allow product to reach ground water, water course or sewage system. Danger to drinking water
confirmed that, in addition to flap angle, blowing across the trailing edge flap can be used to adjust the range of lift coefficients over which extensive laminar flow.. can
In the Women’s Health Initiative (WHI) study, postmenopausal women who had no leisure time physical activity significantly increased their risk of hip fracture by 64%
The effect of X rays on insemination success and retention of sperm during storage in inseminated females was studied by direct microscopic estimates of the
Monitoring land cover dynamics using linear kernel-driven BRDF model parameter
This preliminary research on the accumulation of heavy metals in the sediment of the stabilization ponds with the Hydrocotyle ranunculoides filter in theee areas above