Survey on threats and attacks in cloud infrastructure
Full text
Figure
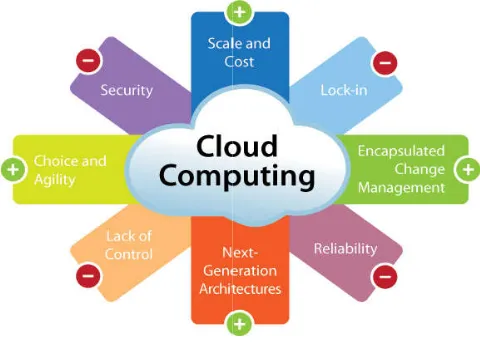


Related documents
Steve Peers, Professor of Law, University of Essex One issue that has arisen in the UK's renegotiation of EU membership is the procedure for the UK (or other Member States) invoking
Non-operating Expenditures: the sum of Enterprise Operations, Non-instructional – Other, Community Services, Adult Education, Non-elementary-secondary programs – Other,
In this paper, we have proposed two novel exploration schemes to learn on-line and on-policy an optimal dialogue management strategy using reinforcement learning.. The key feature
shows how the slot values of an interaction represented at dialogue act level are compressed according to the user goal constraints given in Table ??... it can be seen, this
Most policymakers agree that the main issues in CIR include increased border security and immigration enforcement, improved employment eligibility verification, revision of
Operational efficiency measures lead to YoY EBITDA growth, investment continued amidst pandemic uncertainty. Prudent operational measures helped to grow
Rock Cleaning and Clod-Breaking Device: a device for removing fines from coarse aggregate particles and for breaking up clods without appreciably reducing the natural
ATutor is an Open Source Web-based Learning Content Management System (LCMS) designed with accessibility and adaptability in mind.. Administrators can install or update ATutor