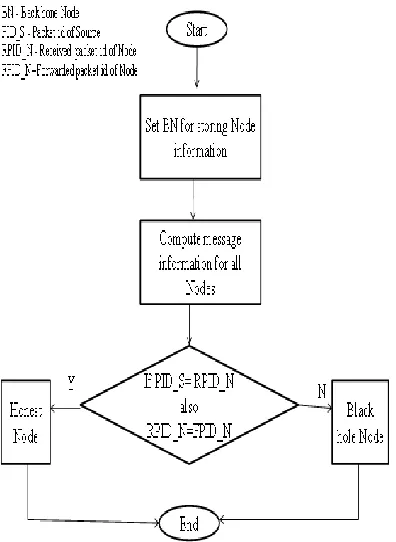
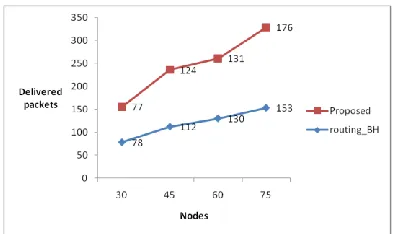
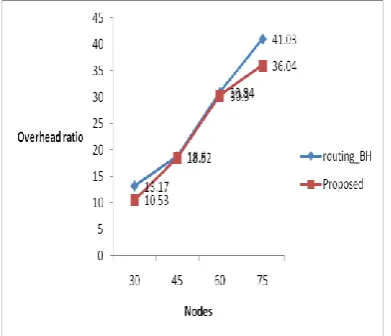
Black Hole Attack Detection And Prevention in Wireless Networks
Full text
Figure
Related documents
The impact of first birth obstetric anal sphincter injury on the subsequent birth a population based linkage study Ampt et al BMC Pregnancy and Childbirth (2015) 15 31 DOI 10
Presented was an optimized AFPM brushless DC motor, the design was aided by Genetic Algorithm and Finite Element Analysis. GA sought to obtain the maximum power per volume for a 1
Attribute Based Encryption(ABE) is a scheme in which users attribute set is used for generation of secret key and it uses access structure that control the access to the data..
Keywords : Carrier Frequency Offset (CFO) estimate, Orthogonal Frequency Division Multiplexing (OFDM), Inter Carrier Interference (ICI), Minimum Mean Square Error
Linear vector algorithms are used in this method. Denoising does not occur with higher power noise. It does not apply to all noise method. The proposed method comes from the idea
Next, the article has the following structure: Section 2 presents an introduc- tion for the neutrosophic representation of information; Section 3 presents the metric for gray
Among the possible approaches (statistical and process based) to predict floods in ungauged basins, many researchers have traditionally applied regression-like region- alisation