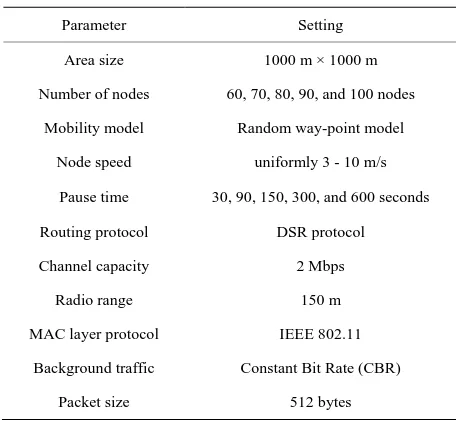
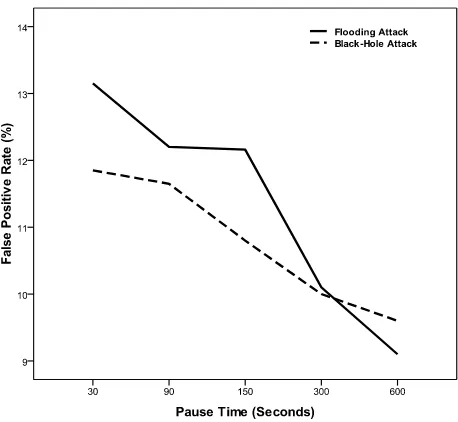
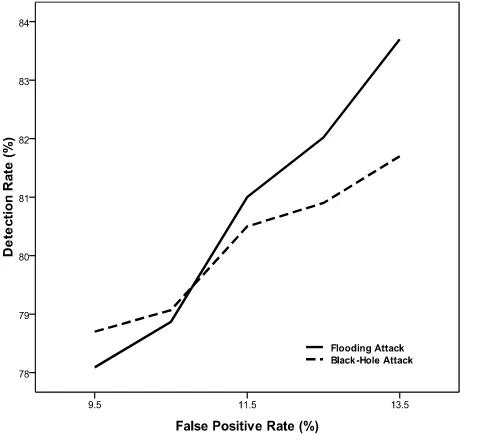
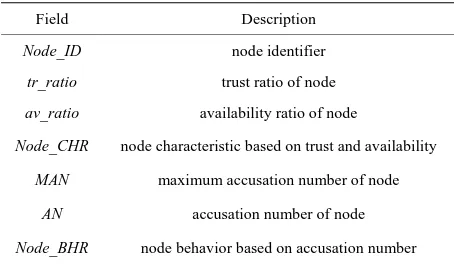
Distributed and Cooperative Anomaly Detection Scheme for Mobile Ad Hoc Networks
Full text
Figure


Related documents
Ties with FBK Dummy variable assuming value 1 if the candidate complies with at least one of the following criteria, and value 0 otherwise: 1) a co-author with a member of
Variabel bebas dalam penelitian ini adalah rasio Kinerja keuangan , Good corporate governance dan corporate social responsibility , dan yang menjadi variabel
There are also TR nodes that correspond to no MultiNet concept (typically, the node representing the verb “be”) and TR nodes corresponding to a whole subnetwork, e.g., Fred in
Social support among HIV positive and HIV negative adolescents in Umlazi, South Africa changes in family and partner relationships during pregnancy and the postpartum period Hill et al
BioMed Central World Journal of Surgical Oncology ss Open AcceResearch Skin invasion and prognosis in node negative breast cancer a retrospective study Keiichiro Tada*1, Hidetomo
In decrypted domain contains firstly decryption of video using encryption key and then extract data using data hider key.. If the codeword belongs to code space C0 then
A Monthly Double-Blind Peer Reviewed Refereed Open Access International e-Journal - Included in the International Serial Directories.. International Journal in Physical &