Data Security using Encryption on Multi Cloud
Full text
Figure

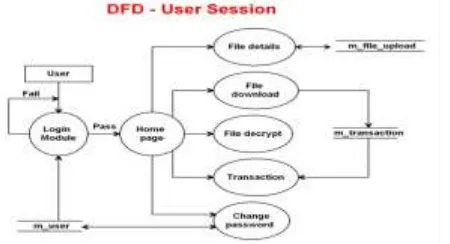

Related documents
In response to this attention, the Vascular and Interventional Radiology (VIR) clinic in the University of Kentucky Healthcare (UKHC) hospital instituted a retrospective review
Early Evidence for a Role of Chromosome Architecture in Fly Genome Function 6 Partitioning of the Drosophila Genome into Domains with Discrete Chromatin Types 8 The Hierarchical
For studying the critical limit of minimum surface roughness that can be achieved by the optimum fluid con- centration, a fresh primary-finished FDM workpiece sample was
ft415 pdf Unc 5/netrin mediated axonal projection during larval serotonergic nervous system formation in the sea urchin, Hemicentrotus pulcherrimus KOUKI ABE, TOMOKO KATOW, SHIOH OOKA
CUAJ ? February 2013 ? Volume 7(2Suppl1) ? 2013 Canadian Urological Association rEviEw S18 Cite as Can Urol Assoc J 2013;7(2) S18 S24 Abstract
This study has the goal to conduct interview with design, engineering and business faculties who teach design thinking courses in their departments to explore
So far we have discussed on how to interpret the acceleration signal obtained form the accelerometer and also discussed that we can use double integration