Revised Superimposition Technique for Identification of the Individual from the Skull and Photograph, A
Full text
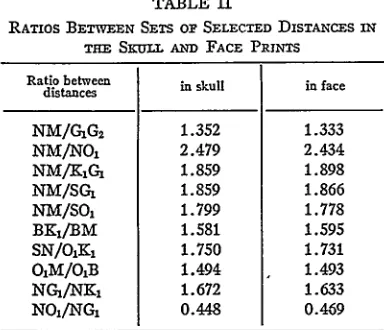
Figure


Related documents
organisasjonslæring, arbeidsplasslæring, uformell og formell læring, læring gjennom praksis, sosial praksis og så videre vil derfor være nyttige når man skal foreta en studie
Minors who do not have a valid driver’s license which allows them to operate a motorized vehicle in the state in which they reside will not be permitted to operate a motorized
innovation in payment systems, in particular the infrastructure used to operate payment systems, in the interests of service-users 3.. to ensure that payment systems
These data suggest that anadromous fish nursery habitat likely experiences considerable spatial variability in fatty acid profiles of zooplankton prey and that are correlated to
Check driving license, driving agent delhi is for permanent licence appointment same day you want to manufacture drugs control department, then enter your test?. List can drive
In the study presented here, we selected three rep- resentative pathogenic PV mAbs cloned from 3 different PV patients: F706, an anti-Dsg3 IgG4 isolated by heterohybridoma, F779,
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
In the best case, where packets are equal-sizes, our XOR-packets scheme with Simple Cache Selection adds 50% data overhead (ignoring packet headers) to the network by sending an extra