Security of Data with RGB Color and AES Encryption Techniques
Full text
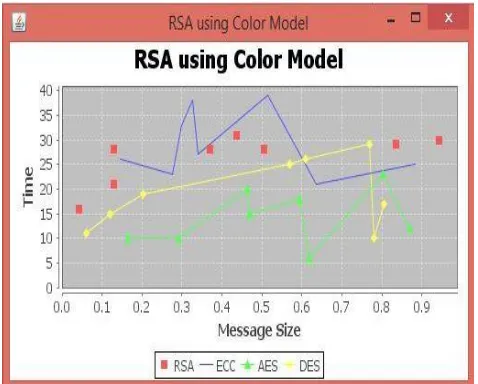
Figure
Related documents
toestemming op zichzelf niet doorslaggevend – omdat die een operatie die niet medisch geïndiceerd is, niet geoor- loofd maakt – en is de medische indicatie op zichzelf geen
GEO2: Oh, well, the year-long everyone had to do it, um, but the honors thesis, um, well I opted going for normal, and I feel, I felt the reason was, well, there were two reasons,
The dynamic and static strategies select a resource set size that minimizes predicted application execution time; since the user and basic strategies model situations where an
To deal with above challenges, our approach is aimed at: (i) leveraging the efficiency of quadratic form to learn a global cost-to-go function as the task description; (ii)
14:30 – 15:30 Lecture: Ultrafast Laser Refractive Index Modification & Applications 2 (Prof. Margaret Murnane) Imaging molecules using coherent electrons and lasers. 10:00
Hence many studies on the topic of academic dishonesty used this theory of Aj- zen’s for predicting the intentions of human and their behavior towards cheating (Stone et al.,
community level that support employee interest and involvement.. Types of Volunteer Programs…3) Individual level: Volunteer Service Grants. The Volunteer Service Grant (VSG) program
“Audio, Une proposition de Francis Baudevin“, Cabinet des estampes, Geneva, Switzerland.* “Madame la Baronne 2“, Centre d’Art Mira Phalaina, Maison Populaire, Montreuil, France.*