CLUSTER HEAD BASED GROUP KEY MANAGEMENT FOR MALICIOUS WIRELESS NETWORKS USING TRUST METRICS
Full text
Figure
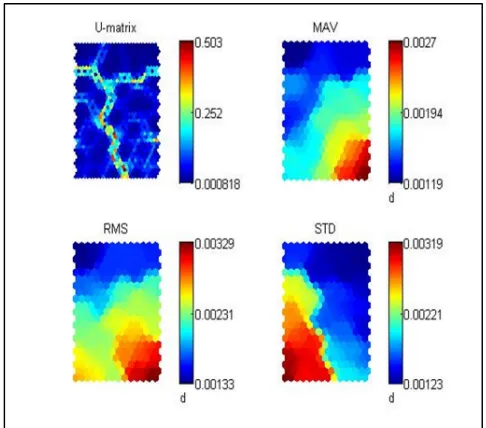
![Figure 1: Rectangle Topology (Two-Dimensional SOM).[3]](https://thumb-us.123doks.com/thumbv2/123dok_us/8911898.959742/2.595.315.555.571.711/figure-rectangle-topology-two-dimensional-som.webp)


Related documents
Abstract— Provision of ductility is of particular importance in the design and detailing of reinforced concrete structures subjected to seismic loads. To fulfill this
common payment method in some Asian countries where credit cards are not available to the general public). The current system can also be developed further as an
People use Flickr in many different ways, holding personal accounts for a variety of reasons. While the two most obvious and functional uses for Flickr are a) a means of sharing photos
For the MLE method, the improvement in estimation of reverberation time parameters when using real measurements is again thought to be due to the real room impulse responses
Dealing with donor organisations, unrealistic ambitions, rigid funding policies and lack of coordination with government organisations have been identified as issues which are




