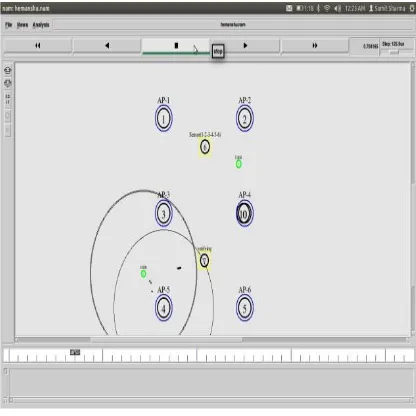
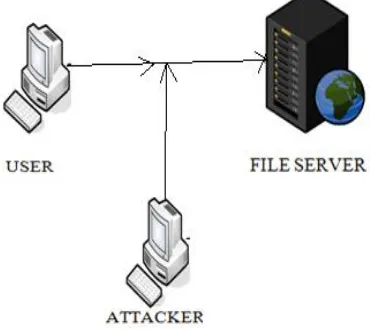
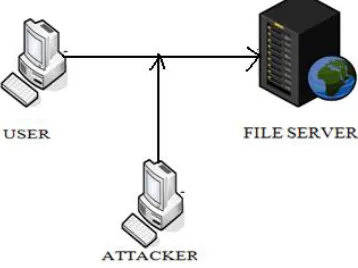
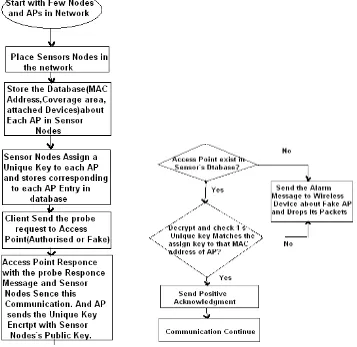
Prevention of Session Hijacking and IP Spoofing With Sensor Nodes and Cryptographic Approach
Full text
Figure
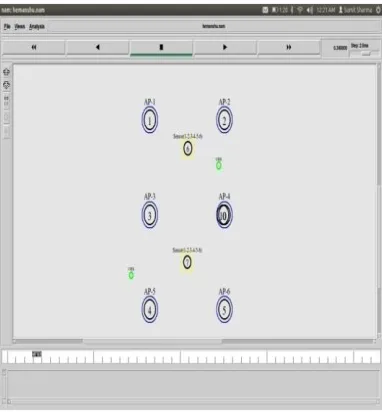
Related documents
The PM shall request the specification of all equipment to be installed in relation to electrical load/weight/heat output, so that he/she can ensure that the correct power delivery
This project in British Columbia is part of the second phase of the Healthy Canada by Design CLASP 1 project, which proposed to build on the tools, expertise, networks, lessons
Workshop segment 3, titled ‘Data collection for research and practice’ provided specific examples from built environment researchers on developing scholarly practice that is aligned
CoStS to dEvEloP intErnal-uSE SoftWarE and WEB SitE dEvEloPMEnt generally, since the technology developed to support cloud services, and the related Web site portal developed as
7: Algorithm of Merchant bank Merchant bank verifies merchant, receives payment message from Client bank through payment server and add payment to Merchant’s
Using an action research strategy and a grounded theory research method, this study has identified critical success factors for the implementation and certification of
Reading and writing skills, communication skills, and analytical, critical, and creative thinking skills are all subject to improve when students learn recognize these patterns
Henderson stated that there came a time when she told the caller that she did not know Reynolds and was not pregnant by him but the calls did not stop.. Defendant took the stand