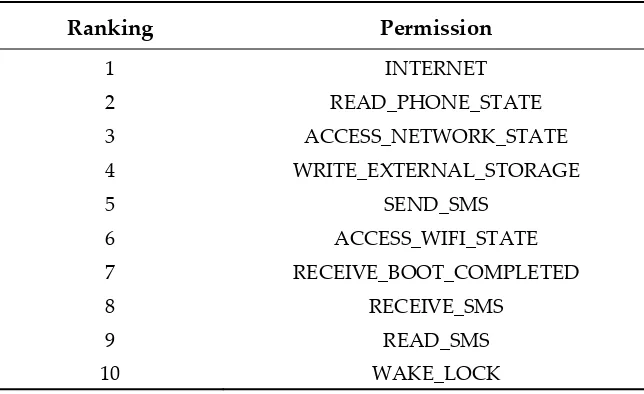
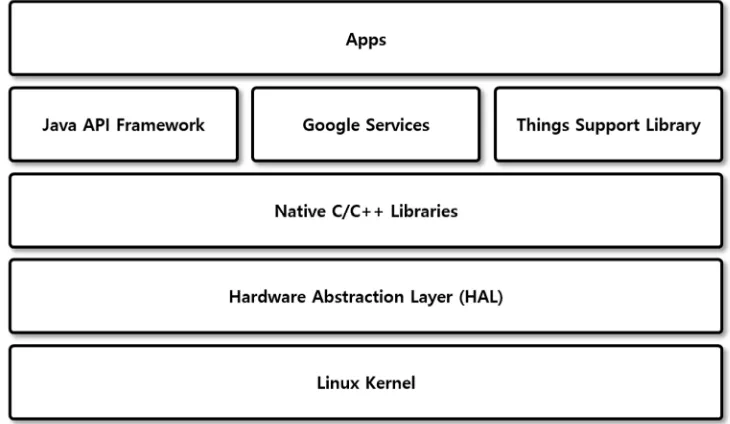
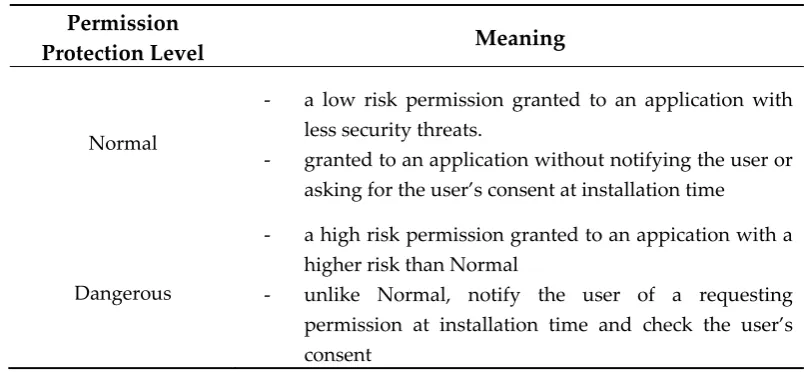
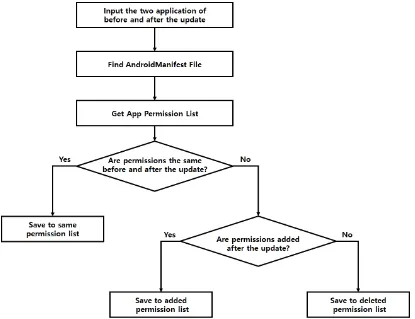
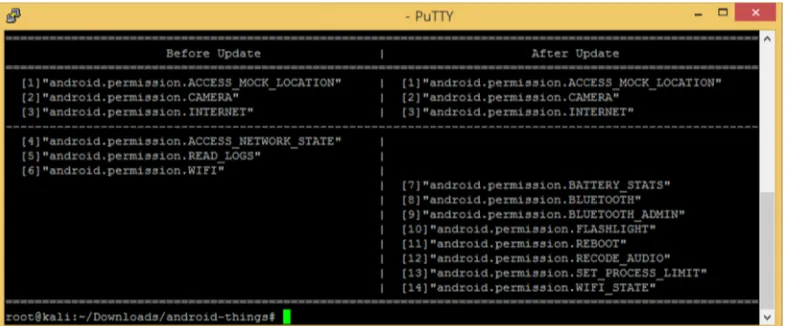
Implementation of Permission Management Method for Before and After Applications the Update in Android-based IoT Platform Environment
Full text
Figure
Related documents
In order to understand the popularity of music tourism, the concept of ‘musical topophilia’ is introduced: an affective attachment to place through and with music. This concept
The quantitative component of the study sought to answer the question: “What is the nature and extent of the relationship between the academic rigour and
Even though they have similar acute or chronic diseases compared to other low-income people, the near poor who have low accessibility have unmet need for health services due
OPERATOR INTERFACE PANEL FIRE ALARM SYSTEM TROUBLE SIGNALS SILENCED POWER ON PRIORITY 2 ALARM SYSTEM SUPERVISORY SYSTEM IS NORMAL 12:35:15 am MON 29 JAN 96
In order to detect the discomfort and fatigue in 3D stereoscopic images, the proposed method detects the excessive disparity regions using the adaptive LoG operator
[1] 2009, Bruce Moulton, Gauri Pradhan, Zenon Chaczko,” Voice Operated Guidance Systems for Vision Impaired People: Investigating a User-Centered Open Source Model”,
The Supreme People’s Court in the Wu Xiaoguang case only held, inter alia, that the court would order an unsuccessful litigant to bear a successful
The CEO and Director of Education and Programs expressed the following desires related to the board: higher attendance at board meetings, higher attendance of board members at