An Improved Three Party Key Exchange Mechanism Using: ECC and Diffie-Hellman with Signature and Verification Algorithms
Full text
Figure
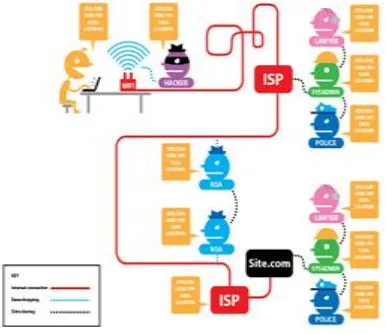



Related documents
Such a rat system provides fairness in society and environment sustainability at the same time since basic needs are supplied at low rate and high rates related to
Pathway analysis results highly suggested that PIK3R3 was involved in cell growth and proliferation (Additional file 1: Figure S1).. To further investigate the potential effect
Poly(vinyl alcohol) (PVA) hydrogels are used to produce high fidelity models for surgical..
ار نآ ناوتب تسا نکمم نيراموک چینام زاب زتنس رد یراتخاس تارییغت يخرب اب هک دهد يم ناشن هعلاطم نيا .دنشاب نداد رارق فده یارب هوقلاب بیکرت
Abstract: In this paper we explored whether engaging in two inquiry skills associated with data collection, designing controlled experiments and testing stated hypotheses,
Based on this evaluation there is little evidence to suggest that a group-based exercise program is more cost-effective than routine care to prevent falls among the
skin ( we hope to the target skin layer)..
Discussion covers the detail results and discussions of the experimentation conducted during this dissertation work, and the various method used the various