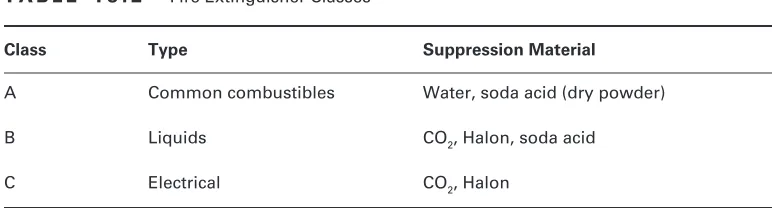
Certified Information Systems Security Professional Study Guide.pdf
Full text
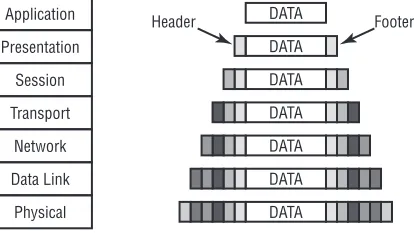
Figure

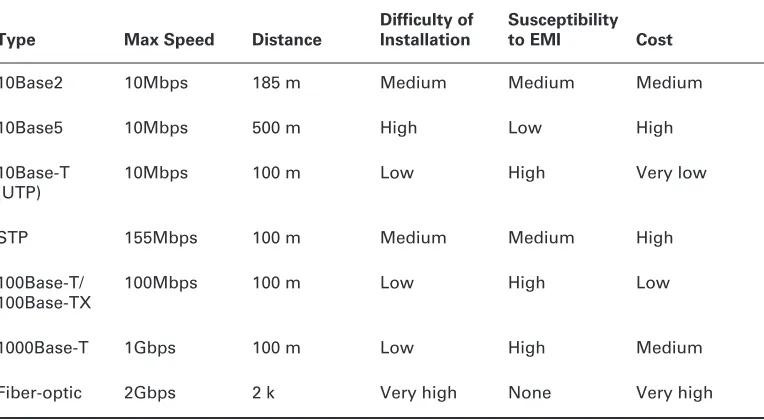

Related documents
Det kan være greit å presisere at disse resultatene representerer hvilken avkastning strategien gir før man tar hensyn til avkastningen i markedet,
Poleg mobilne Android aplikacije je bila izdelana tudi spletna aplikacija, ki sluˇ zi kot vmesnik za dostop do najljubˇsih poti in upravljanje z njimi. Razvoj aplikacije je potekal
Population size structure, growth and reproduction of the European anchovy (Engraulis encrasicolus, L.) in the Lagoon of Lesina (south-western Adriatic Sea,
Based on this rationale, the current study investigated the occurrence of MRSA strains in burn patients and the susceptibility patterns of these strains against various an-
This paper has examined the supposition that participating in the Premier League Kicks initiative provides young Black and minoritised ethnic males with opportunities for
On the other hand, in the simple plastic hinge method, the element stiffness matrix is modified to account for the presence of plastic hinges developed suddenly from an
This research was carried out to determine the effectiveness of the different intervention programs being implemented to curb the spread of HIV pandemic in the country.. The