Analysis of crosscutting concerns in QVT-based model transformations
Full text
Figure
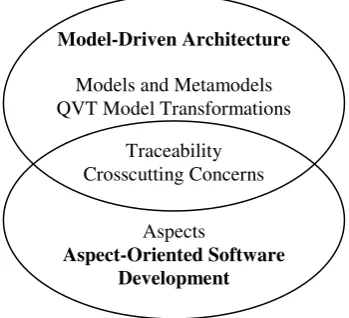
![Figure 2: The MDA Transformation Pattern [17]](https://thumb-us.123doks.com/thumbv2/123dok_us/1164920.1146637/22.595.185.377.68.216/figure-the-mda-transformation-pattern.webp)
![Figure 5: Features of transformation rules [7]](https://thumb-us.123doks.com/thumbv2/123dok_us/1164920.1146637/24.595.102.463.377.682/figure-features-of-transformation-rules.webp)
![Figure 8: Features of rule application strategy [7]](https://thumb-us.123doks.com/thumbv2/123dok_us/1164920.1146637/25.595.208.432.534.652/figure-features-rule-application-strategy.webp)
Related documents
Hacking a Bird in the Sky: Exploiting Satellite Trust Relationship Hack In The Box Security Conference 2008 Artificial Satellite ‣
Apart from counting the number of the art exhibitions organized abroad or sets of Belarusian books presented to diaspora organizations, missing indicators such as the
The system is a follow- on to an early EALAT pilot project of the NASA Land Cover Land Use Change called Reindeer Mapper, which developed a preliminary version of this system
These procedures should be used as part of a larger compliance program in a health care organization or health care setting to detect unauthorized access to electronic protected
size Easy Driver Pro makes getting the Official ASUS F8Sr Laptop Drivers For Windows 7 a snap.. Damage type changed from Lightning to Holy
These include: the extent to which connectivity is increased from online social networks; the extent of linkage between different strengths of relationship and different types
If a signal is generated in the center region of the Nyquist band, all the harmonics created by the non-linear behavior of the generator will show up (folded down) in the same band
The Northwest Palace of Ashurnasirpal II at Nimrud had painted decorations on the ceilings and on the walls above the carved stone blocks that lined the lower walls of the
![Figure 9: Features of rule scheduling [7]](https://thumb-us.123doks.com/thumbv2/123dok_us/1164920.1146637/26.595.143.440.471.649/figure-features-of-rule-scheduling.webp)
![Table 1: UML-to-Relational transformation definition in Relations (partly) [23]](https://thumb-us.123doks.com/thumbv2/123dok_us/1164920.1146637/31.595.100.523.327.642/table-uml-relational-transformation-definition-relations-partly.webp)
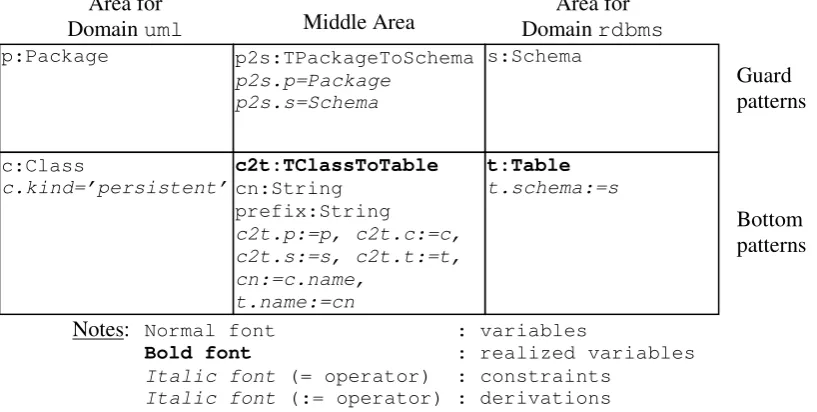
![Table 2: UML to Relational transformation definition in Core (partly) [23]](https://thumb-us.123doks.com/thumbv2/123dok_us/1164920.1146637/35.595.100.521.64.743/table-uml-relational-transformation-definition-core-partly.webp)
![Figure 20: Crosscutting, Tangling and Joinpoints [30]](https://thumb-us.123doks.com/thumbv2/123dok_us/1164920.1146637/40.595.155.464.349.552/figure-crosscutting-tangling-and-joinpoints.webp)
![Figure 22: Concept Diagram of Crosscutting Pattern (without Mapping Concepts) [3]](https://thumb-us.123doks.com/thumbv2/123dok_us/1164920.1146637/43.595.227.414.216.285/figure-concept-diagram-crosscutting-pattern-mapping-concepts.webp)