ETHICAL HACKING: A TECHNIQUE TO ENHANCE INFORMATION SECURITY
Full text
Figure
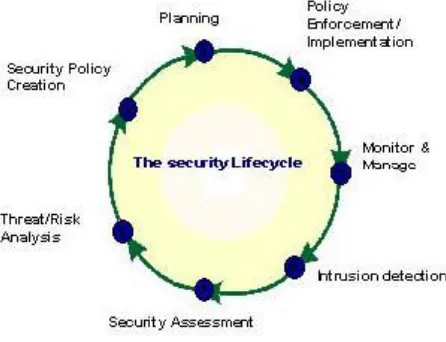
Related documents
ethical hackers to discover the vulnerabilities existing in information systems’ operating environments.”.. With the growth of the Internet, computer
For cylinder blocks without separate bearing plates, refer to section Bearing Plates (page 8) to locate the sealing land surfaces on the cylinder block running surface..
For today’s capital market firms, customer and transactional data generated in standard structured formats like Excel spreadsheets and CRMs is being rapidly outpaced by massive
At the longer horizon, our findings support the asymmetric information hypothesis that the Federal Reserve forecasts embody useful predictive information beyond that contained in
Sitting on his sofa, he takes the glasses again, sees the smear on the right lens and pulls the white cloth from the case to clean them.. He notices, from underneath the cloth,
While under the traditional one-off purchase business model the distributor appears to be shouldering the entire burden of rights protection and security, in the freemium
for: Integrity controls; message authentication; alarm; audit trail; entity authentication; and event reporting.
I should like, particularly, to acknowledge my indebted ness to the Baptist Missionary Society, the Church Missionary Society, the London Missionary Society, the