Network
Luis Andres Cardona
1,2, Bibiana Lorente
1, Sadiel de la Fe
2, Sergio Villar
1, Yi Guo
1, Carles Ferrer
1,2, Alvaro Diaz
Suarez
3, Javier Gonzalez
3, Pablo Sanchez
3, Juan Sancho
4, Juan Rico
4,
Bruno Cendón
41
Instituto de Microelectrónica de Barcelona (CNM-CSIC), 2Universitat Autònoma de Barcelona; Barcelona, Spain
3
Universidad de Cantabria, 4Tecnologías Servicios Telemáticos y Sistemas S.A. (TST); Santander, Spain
Abstract—Among challenging topics in Wireless Sensor
Meshed Networks (WSMNs), security certainly drives many issues. However, it is frequently claimed that standard security mechanisms are prohibitive in WSMNs because they implicate in the extensive use of scarce resource, such as processing power, battery capacity, limited memory, and low bandwidth. Moreover, sensors typically operate in unattended way. Therefore, it becomes very important to propose a feasible way to run the security mechanism in such resource-constrained platform.
This paper will focus in different security aspects of a WSMN application. First, low power is an essential requirement. Thus, measurements of power consumption were performed to improve the accuracy of the security analysis. The objective is to select the best approach (consumption/security) for this specific case but considering that it can also be used for more generic embedded systems. These analyses will be related to different cryptographic methods, secure booting and secure code execution. Second, this cryptography analysis for WSMN is combined with an experimental evaluation of different secure key distribution and storage schemes by using a low cost, low power FPGA. Using this FPGA will enhance the security and computing performance of the platform with lower affection in the power consumption.
Keywords— Secure Booting, Cryptographic, Secure Storage , Wireless Sensor Meshed Network,
I. INTRODUCTION
WSMN application scenarios cover a plethora of applications and also a huge group of devices. Last trends in WSMN aim at reducing costs (microcontroller, devices, peripherals, communication interfaces...) however, due to the potential threats of the applications, the security requirements are getting bigger. In this context it is necessary to develop secure elements to be integrated in devices that assure a certain degree of privacy and trust in all the tasks performed by devices (sensing, processing measurements and wireless transmission).
The overall picture of the WSMN scenario is presented in Fig. 1. It presents the high-level architectural elements of the use case, this represents the whole set of researches that will be done. On the right side it has been depicted the different abstraction level of an element in the architecture, from the network concept to the device level, going through the physical node. On the left side it has been included the simulation model that has been created to evaluate the performance of the different elements that is being changed or evolved. The different levels aforementioned will be used during the
Fig. 1. WSMN architecture
following sections in order to fit the different developments in the right place of the architecture. The most important contributions are:
First, an analysis of what should be the cryptographic strategy used in the booting for WSMN when low power is the main target. This is accomplished by performing realistic measures over the device and by performing these measures over suitable cryptography methods. In addition, a secure execution mode for the WSMN is proposed allowing a low power security for all the working states of the node.
Second, this work is to carry out an experimental evaluation of the secure key distribution and storage schemes for WSMNs. Compared to the previously schemes proposed by Kazienko and Albuquerque [1,2], it is added a Field Programmable Gate Array (FPGA) with the purpose of enhancing the security level of the secret key generated by a pseudorandom number generator (PRNG) at run-time .
The FPGA is mainly responsible for the key management processes. In this scenario, the power consumption caused by its processing is negligible compared to the energy consumption of radio transmission and reception. For security reasons, a large number of external memory cannot be used, therefore, include the FPGA in the system design can definitely strengthen the secure storage and parallel processing capability also as allow flexibility in hardware by using reconfiguration (full or partial) in a future stage. Therefore the base system includes an ARM-based microcontroller connected to a Spartan-6 FPGA. However, a secure communication between the ARM and the FPGA should be guaranteed. This will be described in detail in the Section V.
This paper presents the work that has been done in security improvements of Low Power WSMN scenario. The work is organized as follows. In Section II, a description of the work scope of the TOISE project is presented [21]. Section III briefly describes the system architecture. Section IV refers to secure features for low power WSMNs. Section V presents a secure embedded platform, and Section VI concludes the paper.
II. THE SCOPE OF WORK
Nowadays there are a huge amount of critical facilities which must be protected against attacks. In this scenario, WSMN needs to defense and manage the high impact information which is contained in the infrastructure, and assure the integrity of the data versus attacks.
In order to advance the security in this field, this work is going to deal with different potential weaknesses looking for beyond state of the art secured solutions without negatively impacting the environment. The increase of security levels is a global matter influencing many different aspects of the WSMN. Furthermore, these deployments are intended to be remote managed, so it is also mandatory to create Low Power solutions enabling long life to the devices composing the monitoring network.
Considering the scenario faced by this project, it is derived that the overall use case scope is: “Increase security levels in
WSMN reducing the energy consumption”. More precisely
the use case will develop solutions at different levels; device, node, network and application. Based on this categorization it is easy to identify the different challenges to be overcome:
Device level: the focus at this level will be in providingsecure access to the peripherals in each node and also in allowing more power encryption schemes.
Node level: the efforts at this level will be directed to theprotection against tampering and this kind of attacks derived from physical manipulation.
Network level: includes secured routing protocols thatprevent attacks such as fake nodes, man in the middle, etc.
Application level: it includes all device managementoperations such as: node authorization to be part of the network; secure access to the nodes and the requirements imposed to the applications that will use the information generated by the sensors.
III. SW AND HWARCHITECTURE
Fig. 2. Xynergy Board with ARM CORTEX M4 and SPARTAN-6 FPGA
The design is based on the Xynergy board with an ARM cortex M4 processor and a Spartan-6 FPGA embedded on it as shown in Fig.2. The hardware architecture refers to the identification of a system's physical components and their relationships. The hardware architecture of the sensor and gateway are based on the ones used in the project: the TSmoTe and TSgaTe [3] as shown in Fig.3. The main functions and compositions of each component are depicted below:
Fig. 3. Hardware architecture of enhanced nodes
Microprocessor:
The microprocessor selected for developments is STM32F217IG, which is compatible with the next generation STM32F417IGH6 [4] provided in the Xynergy development boards. This micro has been selected due to the possibilities in term of crypto algorithms included and also because it allows the selective switching on/off different zones of it. Furthermore the envisioned software architecture, based on FreeRTOS is also portable to be used over this hardware element.
Built-in sensors:
The main board of the node includes three built-in sensors directly connected to the ADC converters of the microprocessor. These sensors are:
o
Temperature [5]o
Humidity [6]o
Three-axis accelerometer [7] Communication module:
Communications can be performed through various interfaces. Nodes of WSMN are usually connected through a wireless interface with very low power consumption, including many times proprietary protocols, or open solutions based on IEEE 802.15.4 [8], such as the one developed in this project. Other communication interfaces will be also considered to be included in the main board, mainly cellular network modem or Ethernet socket. In these two cases security features are widely studied and the impact of potential improvements is out of the scope of the work of TOISE project[21].
Secure Flash Memory:
The main requirements of the Flash memory are the consumption and the capacity. The Flash memory of the target node must have the capacity of storing the selected Operating System and the applications that the node runs. Additional data
µC Built-in Sensors Crypto FPGA WSN Com Module Secure Flash Memory External Sensors TSmoTe µC Built-in Sensors Crypto FPGA WSN Com Module Secure Flash Memory External Sensors IP Com Module TSgaTe
!
such as FPGA configuration files may be stored. The stored data must be able to be encrypted. In order to reduce the board consumption, it is important that the memory is a Serial Peripheral Interface Bus (SPI) Flash. Because of the sequential data access, it is possible to reduce the board space, the board consumption and total system cost.
External Sensors:
The architecture of the target node that is being developed allows the insertion of external sensors (i.e. GPS already available using Fastrax IT500 [9]). They are connected to expansion boards properly designed for not comprise node integrity due to sensors vulnerabilities. The communication with these external sensors will be performed using the communication ports included in the board I2C, UART, SPI…
Cryptographic FPGA:
The impact of advanced cryptographic algorithms will be also evaluated along the project in order to compare the enhancement of security features versus the computational and energetic cost of implementing such algorithms in the main board. In order to implement these advanced algorithms an FPGA will be considered for this purpose.
IV. SECURE FEATURES FOR WSNS
In this section, it is explained the main secure features in a low power WSMNs. The scope of this work goes from the initialization of the device (secure boot) to the program execution. To accomplish that it was necessary to perform a study of the more important secure algorithms.
A. Secure Boot
A very important part of the security in WSN is the cryptography method used. This is not only because confidentiality and authentication must be performed but because it is critical that the consumption should not increase significantly compared to a typical non-secure approach. During the booting process, the downloaded embedded firmware needs to be decrypted and/or authenticated to provide security.
1) Cryptography Algorithms
Cryptography methods can be classified into symmetric or asymmetric procedures, depending of the existence of a public key or not. In this work, it is proposed the use of symmetric encryption for the booting process because of three important reasons:
They usually consume less power than asymmetric encryption. This aspect was analyzed in [10][11]
The target platform (STM32) includes specific hardware for symmetric encryption as AES (Advanced Encryption Standard) and triple DES (Data Encryption Standard). The private key can be generated and deployed on the
device during the network initialization phase, simplifying the distribution How this can be performed is explained in Section V.
Furthermore, cryptography security is usually divided in methods that provides authentication and those which provides confidentiality.
To authenticate the downloaded embedded program, a Hash algorithm is usually used and a MAC (Message Authentication Code) signature is obtained. Depending of the desired security level, Hash can be secured by a password (HMAC, hash-based message authentication code). This signature is usually amended at the end of the kernel image. At the receptor, the Hash is calculated from the image and it is compared to the Hash included with the kernel. If the matching is correct, the kernel is authenticated. As it happens with the encryption, the target device from this project provides specific hardware for Hash calculation. The functionality of the available Hash hardware include MD5 (Message Digest Algorithm 5) and SHA-1 (Secure Hash Algorithm 1). MD5 creates a 16 bytes hash while SHA-1 creates a 20 bytes hash, thus SHA-1 is expected to require a little more power consumption than MD5 while providing a little more security.
To provide integrity and confidentiality the kernel has to be encrypted. As it was mentioned, due to the constraints in sensor nodes, symmetric key cryptography is preferred in a WSN. It is worth mentioning that AES is a standardized cryptography method that is the successor of DES. It is a symmetric key cryptographic algorithm that efficiently computes the cipher text of a plaintext using a provided key. This efficiency is results of the fact that within the algorithm only bit-operations like XOR or cyclic shifting are applied. And those can be easily implemented in hardware. The specified block size for AES is 128 bits. The keys can have length of 128 bits, 192 bits or 256 bits [12]. Longer keys provide stronger security guarantees.
2) Secure Boot Process
A secure booting is a necessary feature for a trusted system since it is one of the most vulnerable processes in a WSN system. It is important to ensure that the software that is loaded is trusted software and the system is not corrupted in the booting time. The external FLASH is considered insecure, thus a safe booting methodology is needed when the external flash memory is used for code storage.
The use of an external FLASH memory as storage of the node firmware is justified because of different reasons. For example, sometimes the node stores several firmware in the same location, thus it is possible to load different firmware. Other reason can be the storage of a firmware which memory size is higher than the internal flash memory of the device.
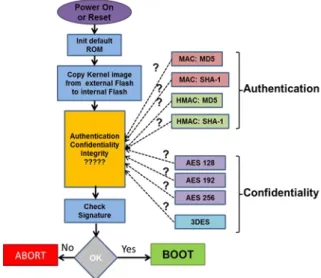
Fig. 4 presents a typical booting process. This booting is the responsible of the access to a secure block of memory, where the firmware is located, and its extraction. Before downloading the firmware from the memory, the memory must be checked to ensure that it is a reliable source. Before the extraction, it is necessary to check the integrity of the firmware. An option to ensure the integrity is to sign the firmware to be loaded. With this solution, it is possible to ensure that the firmware to be loaded is the correct. After this checking, if everything is correct, the loading of the firmware can be executed.
Fig. 4. Different cryptographic possibilities in the booting Specifically, there are the following possibilities for the security in the booting of the platform target: MD5, SHA-1, HMAC-MD5 and HMAC-SHA-1 for authentication and AES-128, AES-192, AES-256 and triple DES for encryption. Those options and how they are implemented are shown with more clarity in Fig. 4. Realistic results have been obtained so an accurate comparison can be performed. The power consumption for a payload of 25600 bytes of the different methods is measured. Those results were obtained for the ECB mode in AES and a microprocessor clock frequency of 120MHz. It is observed that although AES increases 20% for consecutive key sizes in software (these measures were performed in previous simulations) in hardware is different. It is possible to observe an increase of 20% between AES-128 and AES-192 but there is almost no increase between AES-192 and AES-256. Also, TDES can be discarded for its final implementation because not only its security performance is worse than AES but also its consumption is higher. Finally, it is observed that although SHA-1 produces a more collision resistant hash compared to MD5 (20 bytes against 16 bytes), its consumption increases less than 0,5% compared to MD5. In a similar way, the secured HMAC-SHA-1 barely increases the power consumption compared to SHA-1.
B. Secure Virtual Environment
Once the operating system (OS) and the main application are loaded in the memory using a secure boot (and it is a certainty that the firmware loaded is not corrupted), it is necessary to assure that the location of the used memory is secure in order to prevent disturbances. The OS is one of the most typical “entry points” for an attack, thus the modification or update of an OS kernel is critical to the security of the systems.
There are different ways to corrupt the OS when it is loaded and executed in the system. One of the most typical attacks is based on the load of a corrupted application that accesses directly to the OS data or code area. This produces a big problem because if an application has access to the OS, its alteration will be relatively simple. Even an erroneous application developed by the distributor may cause a security hole.
Fig. 5. Memory Scheme
Because of this, the OS must be loaded in a secure memory portion (kernel space) where the accesses by the applications are not made directly. To accomplish this, the use of the Hardware Memory Protection Unit (MPU) is proposed. This unit is integrated in the target device, the STM32F4.
The objective is to create an independent secure kernel space where applications do not have direct access. This allows having the kernel in a safe memory zone, where the applications cannot access, thus preventing attacks through them. Moreover, using the Memory Protection Unit will protect the OS and the authenticated applications from a number of potential errors as system or hardware failures. Fig. 5 shows the proposed memory scheme. It can be appreciated that there are three main sections in this figure. The first section is the operating system table. The second section is the operating system protected by the MPU, and the third section is the location of the applications.
V. KEY MANAGEMENT BY FPGA
Key management involves processes such as key generation, key distribution (exchange), key storage and key replacement. Successful key management is critical for the security of a network where a cryptosystem is deployed, as shown in Fig.6. In this section, an approach to the main system processes will be given to provide the reader a clear understanding of the security improvement achieved by using an FPGA. First it will be detailed how to secure the key distribution and key storage with a security value (Z), randomly generated for that purpose. It will be also explained how to generate such Z values for gate and mote. And finally, how to use the communication link between the ARM and FPGA in a safe way.
Fig. 6. Key management in the Wireless Sensor Meshed Network
A. Secure Key Distribution and Storage
1) Key Distribution Scheme without Secure Storage [18]
The work of Oliveira and Barros [18] propose a key distribution system without the secure key storage. This is a problem because the keys used in the system may be discovered if an attacker captures a regular sensor of the network and the Mobile Node simultaneously.
2) Key Distribution Scheme with Secure Storage [1,2]
The work of Kazienko and Albuquerque [1] considers the need for secure key storage in sensor nodes quite important since they are great in number and their content is, in thesis, more subject to capturing and tampering attempts. Thus, besides security in key distribution it is also intended to provide a larger resiliency and robustness to the system in such a way that the sensors' capturing and tampering will not result in any key discovery.
3) Key Distribution Scheme with Secure Storage in an
FPGA
Fig. 7. Communication between mote and gate
This approach is based on the last two schemes for key secure distribution and storage, but taking advantage of the FPGA capabilities to enhance the secret key security level by loading different PRNG. This is depicted in Fig 7.
Ki(X): Encryption keys for the motes in the network. Before
starting the network operation, an initial K0(X) is present.
Zj(X), Zn(X): Security storage values for mote and gate
generated in their respective FPGAs.
In the pre-distribution or initialization phase, the predefined value K0(X) should be replaced by a new key Ki(X). In this
step, the new key is transmitted from the gate to the mote combining (XOR) the new key Ki(X) with the previous key
K0(X). Never a single key is transmitted alone. Once received
in the mote, this combined value is used along with K0(X) to
obtain the new key Ki(X). To secure the storage of such key, a
security value Zj(X) is required. The generation of Zj(X) is
explained in the next subsection.
Once the system is operating, the communication between gate and mote involves the steps depicted in Fig 7. Steps (1) to (7)
may happen in both the mote and the gate. The steps (6) and (7) change depending on the direction of the communication. Encrypt (6) to transmit or decrypt (7) after reception. Considering the communication from the mote to the gate: (1)Zj(X) and Zn(X) values for the keys’ secure storage are
generated by the FPGA using a PRNG. This value must be known by the ARM in a certain time and be stored in a safe location such as the MPU.
(2)Zj(X) is used to store the encryption key Ki’(X)=E(Ki(X),
Zj(X))
(3)When the ARM needs to encrypt (or decrypt) a message, the key Ki(X) is required. The ARM asks the FPGA to get
this value, but to guarantee a secure transmission through the SPI channel, Ki(X) encrypted with Zj(X) is obtained
(m1’).
(4)The ARM uses the shared Zj(X) to decrypt m1’.
(5)The key Ki(X) to encrypt the messages is available
(6)The encryption of the message(s) takes place and the encrypted message M’ is sent to the gate by the wireless channel.
(7)The gate follows the same steps as the mote to get the key Ki(X) to decrypt M’ and gets the message M=D(M’, m1).
B. Z values generation
In the proposed system two types of encryption schemes can be used: the symmetric keys and the asymmetric keys. Keys can be randomly generated using a Pseudo Random Number Generator (PRNG) or True Random Number Generator (TRNG). TRNG measures some physical phenomenon that is expected to be random and then compensates for possible biases in the measurement process. PRNG uses mathematical algorithms that produce long sequences of apparently random numbers, which are in fact completely determined by an initial value, known as a seed. A pseudo random number will be hard to guess if it is generated into a large enough sequence. A hardware PRNG implemented in a FPGA will be used, in order to generate the secure storage keys for the mote and gate.
Fig. 8. Example of 4 bits LFSR based on polynomial x4+x+1 The PRNG is based on a Linear Feedback Shift Register (LFSR) [17], which is a shift register whose input bit is a linear function of its previous state as shown in example of Fig.8. The only linear function of single bits is exclusive-or (XOR), thus it is a shift register whose input bit is driven by the exclusive-or of some bits of the overall shift registers value. The initial value of the LFSR is called the seed, and because the operation
!
of the register is deterministic, the stream of values produced by the register is completely determined by its current state. Likewise, because the register has a finite number of possible states, it must eventually enter a repeating cycle [18].In order to have the maximum period for the sequence, irreducible polynomials must be used. These polynomials guarantee 2n-1 numbers in a LFSR with n registers [19]. Some of them are:
x32+x22+x2+x+1 x32+x31+x3+x+1 x32+x14+x6+x+1
The idea is to select different polynomial functions to make sure that generated Z is close to a truly random value. The PRNG is generated in VHDL using eight 32 bits LFSR.
C. Secure Communication
Fig. 9. Work Trusted Zones and Secure Communication
A number of research claimed that the cryptographic mechanisms demand plenty of resource from the sensor board in the WSMN (i.e. memory, computing power, power consumption etc.) [13,14]. Moreover, sensors typically operate in unattended way. Therefore, it becomes very important to protect sensitive data stored in sensors, as well as cryptographic keys [15,16]. There are some potential advantages of using the FPGA to release certain tasks of the processor and analyze power consumption and computing power issues. In addition, it allows solving the secure memory storage issue as shown in Fig.9. Consequently the secure communication between processor and the FPGA is required.
The platform is composed by the ARM system (left) and MicroBlaze (MB) system (right), which is implemented in the FPGA. The operation of the whole system is basically composed of two phases.
The first one is the request phase. The ARM system and the MB share an internal key. When a new Zj(X) is requested, the
MB commands PRNG to generate this security value. Zj(X) is
encrypted to be sent to the ARM system by an SPI interface in a secure way.
The second phase is decryption. As soon as the ARM receives the encrypted key Z’j(X), it will use the previous key to decrypt
it. The new decrypted value Zj(X) is used to secure the storage
of the communication keys. During the operation, the attackers can only detect the encrypted key Z’j(X) or the encrypted
communication keys using the internal value Zj (X).
The Zj(X) values are never transmitted over the RF channel.
This is an internal value for every device (mote or gate).
VI. CONCLUSIONS
This paper presents an initial version of the implementation of Low Power Meshed Network security improvements. Specifically some security features for RTOS in WSMN such as secure booting have been shown. It is also presented an analysis of different cryptographic algorithms, with a consumption and security study. Furthermore, a secure virtual environment is proposed to allow a secure operation mode. In addition, the key management has been studied with the dual processor platform on FPGA. Finally the secure key distribution scheme with secure storage was also presented.
VII. ACKNOWLEDGMENT
The authors would like to thank Trusted Computing for European Embedded Systems (TOISE) ENIAC project EUI2010-04240 (JU and Spanish Ministry of Economy and Competitiveness) for their funding support.
REFERENCES
[1] KAZIENKO, J. F.; ALBUQUERQUE, C. V. N. Autenticação, Distribuição de Chaves e Armazenamento Seguro em Redes de Sensores Sem Fio. In: XXXVI Conferência Latino-americana de Informática (CLEI2010), Asunción, Paraguay, 2010, pp.1-14.
[2] KAZIENKO, J. F.; ALBUQUERQUE, C. V. N. Secure Secret Key Distribution and Storage in Wireless Sensor Networks. In: Third IEEE International Symposium on Trust, Security and Privacy for Emerging Applications. Bradford, UK: IEEE Computer Society, 2010, pp.890-895.
[3] TSmoTe and TSgaTe: http://www.tst-sistemas.es/productos/
[4] STM324F417: http://www.st.com/web/en/catalog/mmc/FM141/SC1169/SS1577/LN11
[5] Microchip Low-Power Linear Active Thermistor 9700A. http://ww1.microchip.com/downloads/en/DeviceDoc/21942e.pdf
[6] Honeywell Low voltage Humidity Sensor 5030. http://sensing.honeywell.com/index.php?ci_id=49692
[7] Freescale Semiconductor – Digital Output Accelerometer. http://gadgetgangster.com/scripts/displayasset.php?id=431
[8] IEEE 802.15 WPAN™ Task Group 4 (TG4) : http://www.ieee802.org/15/pub/TG4.html
[9] Fastrax GPS IT500:
http://www.fastraxgps.com/showfile.cfm?guid=7144e100-68d3-493e-adbe-09f77269e045
[10] Yong Wang, Garhan Attebury and Byrav Ramamurthy, “A Survey of Security Issues In Wireless Sensor Networks”, CSE Journal Articles, 2006.
[11] Wei Liu, Rong Luo and Huazhong Yang, “Cryptography Overhead Evaluation and Analysis for Wireless Sensor Networks”, International Conference on Communications and Mobile Computing, 2009.
[12] Announcing the ADVANCED ENCRYPTION STANDARD (AES), Federal Information Processing Standards Publication 197, 2001
[13] Wang, Y., Attebury, G. and Ramamurthy, B. (2006). A survey of security issues in wireless sensor networks. IEEE Communications Surveys & Tutorials, Vol. 8, No. 2.
[14] Kavitha, T. and Sridharan, D. (2010). Security vulnerabilities in wireless sensor networks: A survey. Journal of Information Assurance and Security, 5:31-44.
[15] BECHER, A; BENENSON, Z.; DORNSEIF, M. Tampering with Motes: Real-tampering Physical Attacks on Wireless Sensor Networks. In: 3rd International Conference on Security in Pervasive Computing (SPC), p.1-15, 2006.
[16] HU, F.; SHARMA, N. K. Security Considerations in Ad Hoc Sensor Networks. Ad Hoc Networks, vol. 3, no.1, pp. 69–89, Jan. 2005.
[17] Kumar, Jay; Shukla, Sudhanshu; Prakash, Dhiraj; Mishra4, Pratyush; Kumar, Sudhir. Random number generator using various techniques through VHDL. International Journal of Computer Applications in Engineering Sciences, p. 127, June 2011.
[18] OLIVEIRA, P. F.; BARROS, J. A Network Coding Approach to Secret Key Distribution. IEEE Transactions on Information Forensics and Security, 3(3):414-423, 2008
[19] http://www.hpl.hp.com/techreports/98/HPL-98-135.html
[20] Xynergy board: http://www.silica.com/product/silica-xynergy-m4-board.html
[21] TOISE project website: http://www.toise.eu/