Network Vulnerability Analysis
Full text
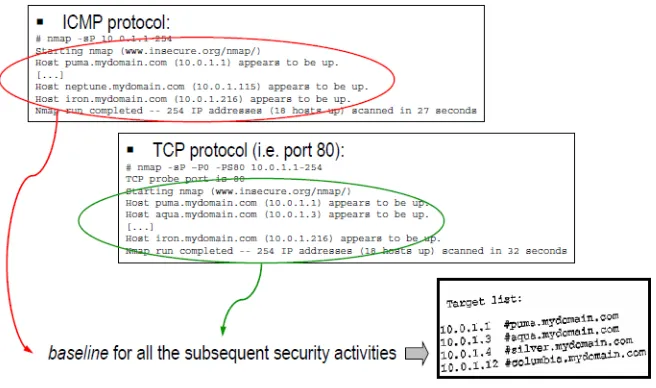
Figure

Related documents
Model 3.2 is estimated with two-stage least squares, with election-year incumbent job approval, challenger spending, and incumbent spending treated as endogenous and the
The determination of a physician’s readiness to perform robotic surgery is solely the responsibility of the hospital, surgical center or medical facility where the procedure
Especially with regards to organizational membership, the weakness of which was confirmed in the survey 13 , this serves to illustrate that internet activism is quite
hyperdivergent subsample demonstrated clinically and statistically significant increases in facial height, increase in maxillary molar eruption, and decreases in overbite post-.. 12
This paper reviewed the literature on pit and fissure sealants under the following subheadings: (1) laboratory studies, (2) clinical technique and tooth preparation, (3) etching
The sample consists of 665 common stocks listed on the NYSE o r NASDAQ that appear on the initial shorting ban list versus a set of 665 matched control firms that are not subject to
Each case would be analyzed, discussed and the cases would be related to the business ethics concept and ethical principle.. This study aims to create good moral value and
We obtained difference-in-differences estimates of the effect of the nurse work hour policies on the likelihood of working mandatory overtime, working more than 40 hours per week,