Karstic aquifer vulnerability assessment methods and results at a test site (Apulia, southern Italy)
Full text
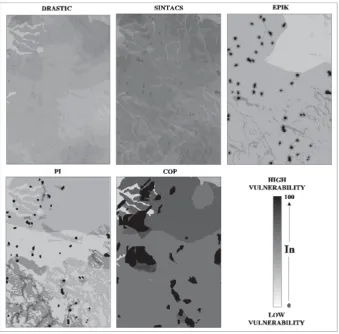
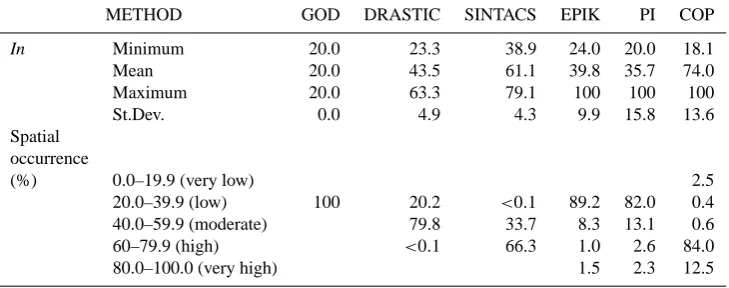
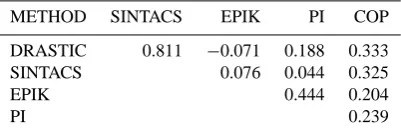
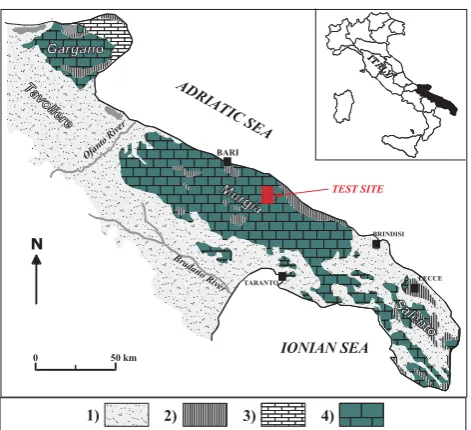
Figure
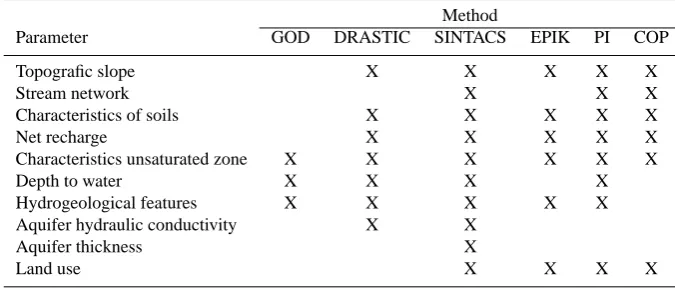
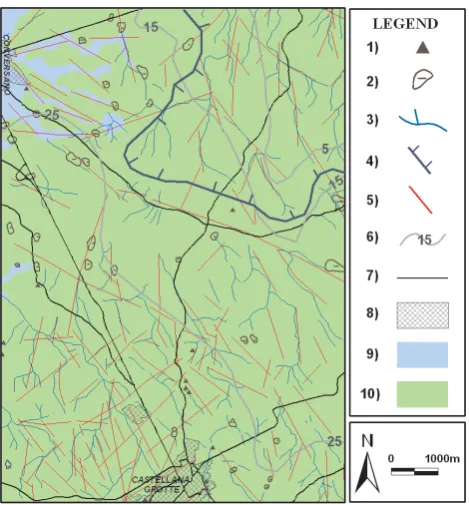
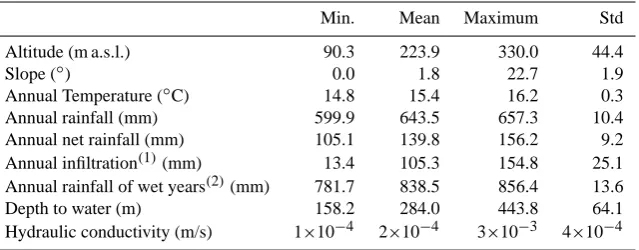
Related documents
The degree of resistance exhibited after 1, 10 and 20 subcultures in broth in the absence of strepto- mycin was tested by comparing the number of colonies which grew from the
We incorporated equations in BDDs directly, without encodings. The resulting objects are called EQ- BDDs. A straightforward notion of ordered EQ-BDDs is dened, and it is proved
Although the impact of marketing and/or operations capability on a firm’s financial performance has been studied (e.g. Song et al., 2005; Terjesena et al., 2011; Nath et al.,
Header (name, address, etc.) back so it’s no longer visible. 2)Fold the employment section of your resume back so it too is no longer visible. 3)What you have left is your 30
The screening was done for the following TTN mu- tations associated with HMERF: p.Gly30150Asp identified in the current study, p.Cys30071Arg recently identified in North
As more businesses adopt cloud-based email security and archiving services, the impetus will be on cloud service providers to operate with total transparency regarding the
Contego’s NAC-as-a-Service is a proven, enterprise-class solution that addresses many security risks for customers—from employee and guest access control, to real-time
The Workflow Management Coalition (WfMC), having the definition of business process, has defined workflow as “The automation of a business process, in whole or part, during which