Recursive Identification of Hammerstein Systems with Polynomial Function Approximation
Full text
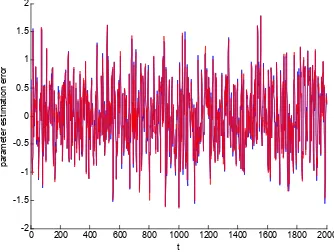
Figure

Related documents
loans from the company law standpoint; instead, subordinated loans have been regulated as a part of equity capital and an order has been established by the respective legal
Cable TV Company Box (demarc) Command Center ™ Video Distribution Panel — Input RG6 Quad Command Center ™ Video Distribution Panel — Output Bedrooms, Family Room, MBR, Office
Thus levels completing forces player to learn new course chapters and solve level assignments, so the game scenario relates to the learning course (Figure 1).. For example,
University of Helsinki Faculty of Social Sciences.. Hence when the assumptions of the Modigliani–Miller theorem and the CAPM hold, the question about the optimal source of funding
The security of the new MixColumns was analyzed, and the NIST Test Suite tests were used to test the randomness for the block cipher that used the new transformation..
This design considers the fingerprint image for the client side security and also considers the AES algorithm for the secured communication in between the client and server..
User Logic SRAM Memory Cells Static Part FPGA AES Application K Encrypted Bitstream Non Volatile Memory (NVM) Bitstream K AES Encrypted Bitstream.. Figure 5.6:
The software engineering object oriented design methodology [13] is appropriate for behavior exploration, but we need to incorporate the structural hardware elements into it..