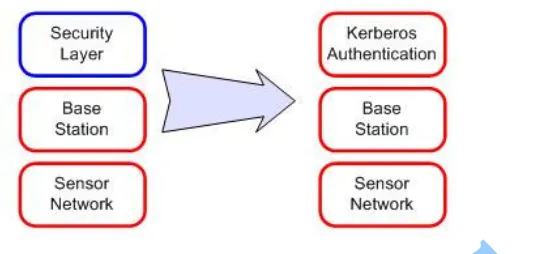
Kerberos Authentication in Wireless Sensor Networks
Full text
Figure




Related documents
Auditors’ Requirements Leverage-able It Infrastructure Negative Security- Related Publicity Accumulating & Inappropriate Privileges Help Desk Overload Continuous Compliance
A capital contribution to reserves that is produced in each of the four utilities (water, wastewater, storm water and solid waste utility business units) may be supplemented
To determine the firmware levels of the DS3400 storage subsystem, the connected storage expansion enclosures, and the installed hard disk drives, use the DS3000 Storage Manager
06 Wood and products of wood and cork (except furniture); articles of straw and plaiting materials; pulp, paper and paper products; printed matter and recorded media 08
Keywords: integration in construction, integrated design, collaboration in construction, inter-disciplinary, interprofessional dialogue, integrated project teams, structural
While this study hypothesizes that these areas in need of special services for female offenders will be concentrated largely in substance abuse, health care, employment, housing,
This article describes how the British Nutrition Foundation Drummond pump priming award was used to initiate a large scale collaborative project called Gene-Nutrient
In the second part of this section, we show a new, orthogonal approach: By summarizing ‘similar’ objects prior to the lattice computation with a standard clustering algorithm