A robust and efficient scheme for image encryption-decryption
Full text
Figure


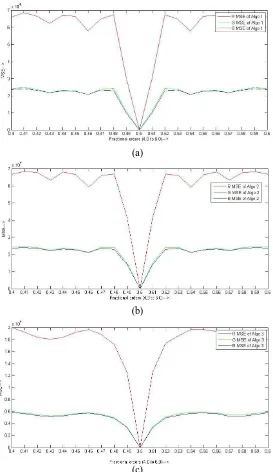
Related documents
‘Boston, Providence and New York Smart Set Out In Force At Jacob’s Hill Horse Show’ Unreferenced newspaper cutting, Dorothy Neyhart Scrapbook Collection, 1922-1935, National
Now here we were, sitting in our Toyota four-wheel-drive at the military base, watching the drug plane drop below the treeline and into the G2 team's jaws. After a few long
Seborrhea (increase in sebum secretion) and sebaceous gland hypertrophy and hyperplasia are the hallmarks of acne [8]. The changes in the quality of sebum may
Institute of Indian Medical Heritage (NIIMH), Hyderabad, central council for Reserch in Ayurvedic Sciences (CCRAS) New Delhi ;
Kekerasan dalam Rumah Tangga dalam Pasal 1 angka 1 UU Nomor 23 Tahun 2004 tentang Penghapusan Kekerasan Dalam Rumah Tangga (PKDRT) disebutkan bahwa kekerasan dalam
Sea ice in Mc- Murdo Sound is atypical of Antarctic pack ice, so improved understanding of the CS-2 freeboard measurement over vary- ing snow and sea ice conditions in open water
Abdullah, Dynamical behavior of SIR epidemic model with non-integer time fractional derivatives: A mathematical analysis, Int. Ahmad, Dynamical behavior
Design of Asymmetric Slot Antenna with Meandered Narrow Rectangular Slit for Dual Band Applications.. Raj Kumar 1, * ,