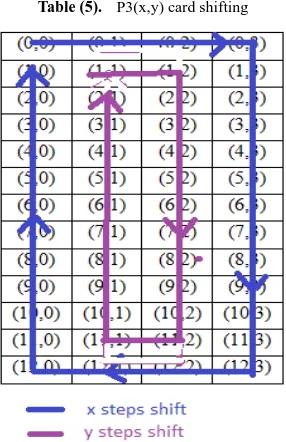
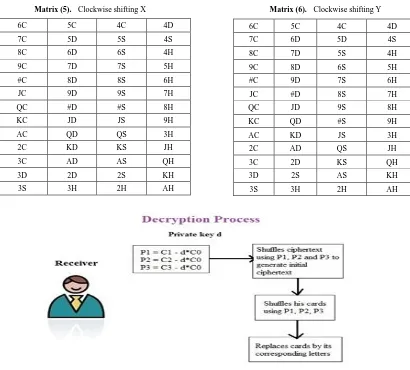
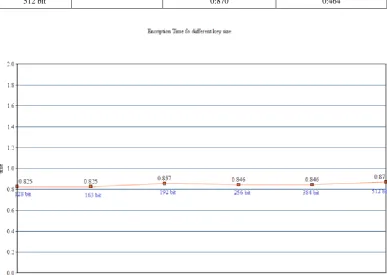
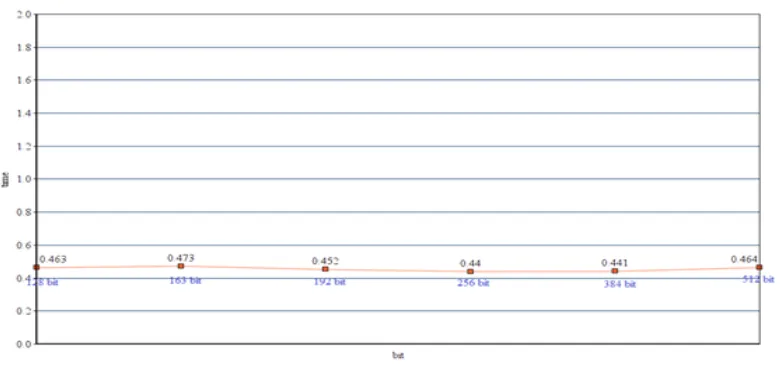
Data and Information Security in Modern World by using Elliptic Curve Cryptography
Full text
Figure

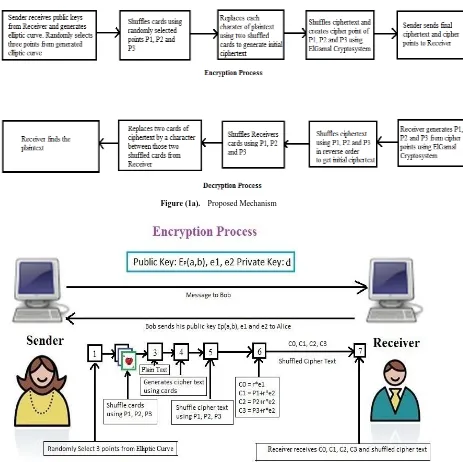


Related documents
cystic fibrosis clinic of the Hospital for Sick Chil- dren over the period 1977 to 1988 revealed that cystic fibrosis patients with insulin-dependent di- abetes meffitus are, for
This corresponds well with the study of Afifi et al., who reported that child abuse is an important determinant of both physical and mental health-related QoL in adulthood [36],
Mechanical design is critical since large mass is moved in this type of web guide; especially the mechanical design requires consideration for the speed, acceleration,
Table 5 Association of maternal characteristics with total phytoestrogen intake among 6,441 mothers of control infants in the National Birth Defects Prevention Study.. Percent of
[3] stated that in coastal lagoons, density stratification which refers to layering of water on the basis of vertical variation in the salinity or temperature
division of India, Pakistan won a poor share of the colonial government's financial. reserves - with 23 percent of the undivided land mass, it inherited only 17.5 percent
On the hand if the traffic is present on the road R2 then the control is sent to state S2 which switches on the signal on road R2 to green and rest of the signals are