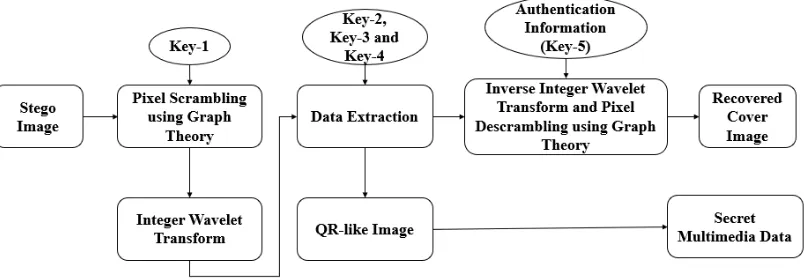
QR like Secret Data Hiding in Integer Wavelet Transform Domain Images
Full text
Figure


Related documents
Swarm accelerometer data processing from raw accelerations to thermospheric neutral densities Siemes et al Earth, Planets and Space (2016) 68 92 DOI 10 1186/s40623 016 0474 5 F U L L PA P
After the first 12 h according to randomization, the anticoagulation management was modified according to the assigned study group: In the TEG group (interven- tion group),
Key words: Self-esteem, perceived self-competence, youth, obesity, weight loss, residential intervention.. Address
ACE 5 angiotensin-converting enzyme; ANRIL 5 antisense noncoding RNA in the INK4 locus; CI 5 confidence interval; CGAS 5 candidate gene association study; EDNRA 5 endothelin
From table 3 we observe that using dedicated path-based protection scheme in network topology A, the total number of protection paths is 6, total working capacity
The precision agricultural system is based on the Global Positioning Systems (GPS), Machine to Machine Communications (M2M), IoT technologies, sensors and Big Data
Because antidumping laws do not assure indigents access to private hospi- tals for nonemergency medical care, public hospitals must provide a high proportion of
This paper suggest architecture of an intelligent warehouse for structured, unstructured and semi-structured web data and an expert system that use to solve all web mining