International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 6, June 2014)
619
Performance Analysis of Symmetric Encryption Algorithms for
Mobile ad hoc Network
Sunil Kumar Sahu
1, Ajay Kushwaha
21
M. Tech Scholar, 2Associate Professor, Computer Science & Engineering Rungta College of Engineering & Technology Bhilai (CG), India
Abstract—Nowadays applications on internet are growing rapidly, everyone shares their thoughts, feelings, personal data and many more information online, that’s why security is one of the most considerable and important factor in wireless network. Symmetric key Cryptography algorithm is widely used to provide security. In this paper we are implementing symmetric key encryption algorithms in ns2 to compare performance of various symmetric key algorithms with different data types like text and image based on some performance metrics to find out best algorithm to use in future.
Keywords—Symmetric key algorithm, AES, DES, BLOWFISH.
I. INTRODUCTION
During this time when the Internet provides vital communication between tens of millions of people and is being more and more used as a means for E-commerce, security becomes a greatly important issue to deal with. In wireless network, Cryptography acting a major role. Basically Cryptography is the procedure of hiding data or information. They can be separated into two part i.e. symmetric key and asymmetric key algorithm. In Symmetric key Cryptography algorithm, there is only one private key that is common between sender and receiver to encrypt/decrypt data. Symmetric key algorithms are also two types: block ciphers and stream ciphers. Block ciphers are using on group of blocks, for example AES (Advanced Encryption Standard), DES (Data Encryption Standard) and Blowfish. Stream ciphers are using on single bit at a time ,for example RC4.In Asymmetric key algorithm there is two different key private/public for encryption and decryption, one is public key which is used for encryption while another is private key which is used for decryption, for example RSA algorithm. Public key is recognized to public and private key is only recognized to user. Due to large computational processing power asymmetric key algorithm is 1000 times slower than symmetric key algorithm.
Fig 1.1 shows the hierarchy of computer.
Fig1.1 Hierarchy of cryptography 1.1 Goals of Cryptography
1.1.1Confidentiality
Confidentiality is basically used to ensure that data remains private which is usually achieved using encryption.
1.1.2 Data integrity
Data integrity is used to ensure that data is secured from accidental or malicious change.
1.1.3 Authentication
Authentication is used to assure that correct originator of data must be known to receiver.
1.1.4 Non Repudiation
Non Repudiation is used to assure that the sender of the message cannot deny having sent the message or receiver cannot deny about received message.
1.2 Symmetric Key Algorithm
DES: Data Encryption Standard (DES) was the first
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 6, June 2014)
620 Basically DES uses one 64 bits key with 64 bits block, out of 64 bits key, 56 bits are used to decide the exact cryptography alteration and remaining 8 bits are used for error discovery. In DES there are total 16 rounds to execute their operations; the main operation in each round is permutation and substitution. The result of DES encryption is 64 bit cipher text. Decryption in DES is same as encryption, only the keys are applied in reverse order.
[image:2.612.327.562.136.285.2]Fg 1.2 shows the concept of symmetric key algorithm.
Fig.1.2 Symmetric Key algorithm
AES: The FEDERAL INFORMATION PROCESSING
STANDARDS PUBLICATION (FIPS) specifies the AES (Advanced Encryption Standard) also recognized as Rijndael (Rain-doll) after introducing the DES. It is also Block cipher encryption standard that uses 10, 12, or 14 rounds with 128,192 or 256 bits sizes key depending on the number of rounds. Each processing round consist of four steps –
1. Substitute bytes
2. Shift rows
3. Mix columns
4. Add round key
Blowfish: Blowfish is another element of symmetric block cipher encryption normal that is developed by Bruce Schneier in 1993 and it can be professionally used for encryption and decryption of data considerably. Basically it has variable length key from 32 bits to 448 bits. It is license-free, and is available for all uses. Blowfish is fast i.e. encryption rate on 32 bit microprocessor is 28 clock
cycles/sec. Basically Blowfish is appropriate for
applications where the key leftovers constant for a long interval of time.
1.3 Asymmetric Key Algorithm
Asymmetric key algorithm is fairly different than Symmetric key algorithm which previously discussed earlier. There is two different key for encryption and decryption, one is public key which is used for encryption
while another is private key which is used for decryption.
Fig 1.3 shows the concept of Asymmetric key algorithm.
Fig 1.3 Asymmetric key algorithm
II. LITERATURE REVIEW
To give more approaching about the performance of the compared algorithms, this part discusses the outcome obtained from other resources. In [2] it is found that after only 600 encryptions of a 5 MB file using Triple-DES the remaining battery power is 45% and subsequent encryptions are not possible due to battery dies rapidly. In [3] it is concluded that AES is faster and more efficient than other encryption algorithms. When the broadcast of data is considered there is insignificant difference in performance of different symmetric key schemes. Under the scenario of data transfer it would be better to use AES scheme in case the encrypted data is stored at the other end and decrypted multiple times.
[4] presented a performance analysis between four most common algorithms: DES, 3DES, AES, and Blowfish. The judgment had been done by running several different settings to process different packet of data blocks to calculate the algorithm’s encryption/decryption speed. The simulation setup was in C# programming language. The results of this paper shows that blowfish has a better performance than other common encryption algorithms. AES showed poor performance results compared to other algorithms since it requires more processing power.
[5] provided the popular secret key algorithms together with DES, 3DES, AES (Rijndael), Blowfish, were implemented, and their performance was compared by encrypting input files of varying data sources and sizes.
Here the algorithms were implemented in Java
programming, and were tested on two different hardware platforms, to present the comparison. The two different equipment are: P-II 266 MHz and P-IV 2.4 GHz.
[image:2.612.51.284.249.336.2]International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 6, June 2014)
621 [7] Presented a comparison of AES, DES, 3 DES, RC2, Blowfish and RC6. They used different settings for each algorithm such as different sizes of information blocks, different data types, battery power consumption, dissimilar key size and ultimately encryption/decryption speed. They done that in case of changing packet size Blowfish showed better performance than other algorithms followed by RC6.
AES had better show than RC2, DES, and 3DES. In case of changing key size – it was concluded that higher key size leads to clear change in the battery and time consumption.
[8] Presented a qualified analysis between AES along with RC4 for better utilization. In this paper authors tried to locate out performance comparison between block ciphers (AES) and stream cipher (RC4) standard. Based on the analysis and result, this paper finished that which algorithm is better to use based on different performance metrics. The a variety of metrics were: Encryption time, Decryption time, Throughput, CPU process time, Memory Utilization.
It was over in [9] that AES is faster and more proficient than other encryption algorithms. Increasing the key size by 64 bits of AES leads to increase in energy consumption about 8% without any data transfer. The difference is not obvious. Reducing the number of rounds leads to power savings but it makes the protocol insecure for AES and should be avoided.
[11] Presented AES algorithm that describes the effective security for data storage in mobile devices by implementing for encryption and decryption and finds that embedded systems similar to Mobile phones, GPS receivers, Wireless Sensor Nodes etc hold sensitive data, hence requires data security mechanisms. AES algorithm which is a standard algorithm for data encryption is appropriate for such scenarios where memory and processing power constraints are very high.
III. METHODOLOGY
In this work the various encryption algorithms have been implemented in ns2 and the research has been carried out using a laptop, with Intel(R) Core(TM) i3-2310M CPU @ 2.10 GHz, 2100 MHz, 2 Core(s), 4 Logical Processor(s). In the experiments, the algorithms encrypt a different file formats like text and image files with file size ranges from 256 to 512 Bytes. The performance metrics like encryption time, decryption time, battery consumption, residual battery and throughput have been together for each type of file. The encryption time is the time that an encryption algorithm takes to produce a cipher text from a plain text. The decryption time is the time that decryption algorithm takes to produce a plain text from a cipher text.
Encryption time is used to calculate the throughput of an encryption plan. The throughput of the encryption method is intended as the total plain text in bytes encrypted divided by the encryption time [10].
The figure 3.1 shows the screen shot showing the basic 42 mobile nodes in MANET.
[image:3.612.324.562.270.617.2]Fig. 3.2 shows the data transfer between source and destination of data in MANET.
Fig 3.1 Basic mobile nodes in MANET
Fig. 3.2 Data transfer from source to destination in MANET
IV. RESULT AND DISCUSSION
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 6, June 2014)
622
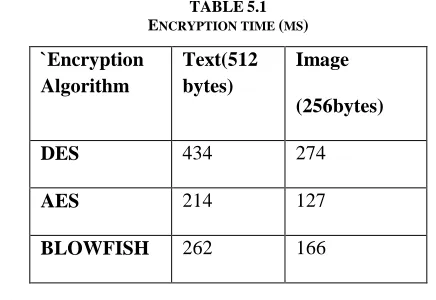
5.1 Encryption time
Table 5.1 shows the encryption time in milliseconds against 20 milliseconds of simulation time for DES, AES and BLOWFISH encryption algorithms for text and image files.
TABLE5.1 ENCRYPTION TIME (MS) `Encryption
Algorithm
Text(512 bytes)
Image (256bytes)
DES 434 274
AES 214 127
BLOWFISH 262 166
5.2 Decryption time
Table 5.2 shows the decryption time in milliseconds against 20 milliseconds of simulation time for DES, AES and BLOWFISH encryption algorithms for text and image files.
TABLE5.2 DECRYPTION TIME (MS)
5.3 Throughput
Table 5.3 shows the Throughput in kbps against 20 milliseconds of simulation time for DES, AES and BLOWFISH encryption algorithms for text and image files.
TABLE5.3
THROUGHPUTS (KBPS)
5.4 Battery consumption
Table 5.4 shows the battery consumption in joules against 20 milliseconds of simulation time for DES, AES and BLOWFISH encryption algorithms for text and image files.
TABLE5.4
BATTERY CONSUMPTION (JOULES)
5.5 End to end delay
Table 5.5 shows the end to end delay against 20 milliseconds of simulation time for DES, AES and BLOWFISH encryption algorithms for text and image files. Decryption
Algorithm
Text (512 bytes)
Image (256 bytes)
DES 451 269
AES 221 129
BLOWFISH 253 157
Throughput
Text (512 bytes)
Image (256 bytes)
DES 28.13 14.6
AES 5.27 2.92
BLOWFISH 35.20 18.26
Battery Consumption
Text (512 bytes)
Image (256 bytes)
DES 83.087 79.0502
AES 72.087 71.8365
[image:4.612.334.539.134.304.2] [image:4.612.54.272.203.353.2] [image:4.612.327.532.385.536.2] [image:4.612.44.268.427.569.2]International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 6, June 2014)
623 TABLE5.5
END TO END DELAY (MS)
5.6 Residual battery
Table 5.6 shows the residual battery in joules against 20 milliseconds of simulation time for DES, AES and BLOWFISH encryption algorithms for text and image files.
TABLE5.6
RESIDUAL BATTERY (JOULES)
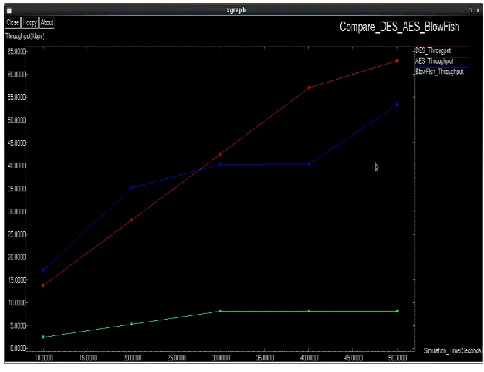
[image:5.612.320.576.127.349.2]Fig 5.1 shows the graph for comparison of encryption time for various algorithms against 10-50 milliseconds of simulation time where x-axis shows the simulation time (sec) and y-axis shows the encryption time (ms).
Fig 5.1 Encryption time of Symmetric Algorithms
[image:5.612.68.252.159.284.2]Fig 5.2 shows the graph for comparison of decryption time for various algorithms against 10-50 milliseconds of simulation time where x-axis shows the simulation time (sec) and y-axis shows the decryption time (ms).
Fig.5.2 Decryption time of Symmetric Algorithms End to End
Delay
Text(512 bytes)
Image(256 bytes)
DES 48.7766 32.3504
AES 49.1367 34.1229
BLOWFISH 48.7349 32.3178
Residual Battery
Text (512 bytes)
Image (256 bytes)
DES 24.543 28.9498
AES 35.7653 36.1635
[image:5.612.56.277.371.498.2] [image:5.612.332.576.406.611.2]International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 6, June 2014)
[image:6.612.57.299.197.383.2]624 Fig 5.3 shows the graph for comparison of throughput for various algorithms against 10-50 milliseconds of simulation time for various algorithms where x-axis shows the simulation time (sec) and y-axis shows the throughput (kbps).
Fig 5.3 Throughput of Symmetric Algorithms
V. CONCLUSION AND FUTURE WORK
In order to provide protection to digital multimedia content from hacking or stealing, cryptography is performed over the network, by performing encryption and
decryption into any multimedia file (audio or video). The
obtainable simulation results showed that AES is better for encryption, decryption and residual battery and also it has more End to End Delay. But when we are comparing encryption speed i.e. throughput, BLOWFISH has better performance than other common encryption algorithms used but BLOWFISH has more battery consumption than other algorithms. In future we work on comparison of security for symmetric key algorithms.
REFERENCES
[1] M.Umaparvathi1, Dr. Dharmishtan K Varughese ―Evaluation of Symmetric Encryption Algorithms for MANETs ―978-1-4244-5967-4/10/$26.00 ©2010 IEEE
[2] Ruangchaijatupon, P. Krishnamurthy,‟ Encryption and Power Consumption in Wireless LANs-N,‟‟ The Third IEEE Workshop on Wireless LANs -September 27-28, 2001- Newton, Massachusetts.
[3] Nagesh Kumar, Jawahar Thakur, Arvind Kalia on ―PERFORMANCE ANALYSIS OF SYMMETRIC KEY CRYPTOGRAPHY ALGORITHMS: DES, AES and BLOWFISH ― in An International Journal of Engineering Sciences ISSN: 2229-6913 Issue Sept 2011, Vol. 4 ,pp.28-37
[4] Tamimi, A Al; ―Performance Analysis of Data Encryption Algorithms‖, Oct 2008.
[5] Nadeem, Aamer; "A Performance Comparison of Data Encryption Algorithms", IEEE 2005.
[6] Penchalaiah, N. and Seshadri, R. ―Effective Comparison and Evaluation of DES and Rijndael Algorithm (AES)‖, International Journal of Computer Science and Engineering, Vol. 02, No. 05, 2010, 1641-1645.
[7] Elminaam, D S Abd; Kader H M Abdual and Hadhoud, M Mohamed. ―Evaluating the Performance of Symmetric Encryption Algorithms‖, International Journal of Network Security, Vol. 10, No. 3, pp. 216-222, May 2010.
[8] Singhal, Nidhi and Raina, J P S. ―Comparative Analysis of AES and RC4 Algorithms for Better Utilization‖, International Journal of Computer Trends and Technology, ISSN: 2231-280, July to Aug Issue 2011, pp. 177-181.
[9] S.Hirani, ''Energy Consumption of Encryption Schemes in Wireless Devices Thesis,'' university of Pittsburgh, April 9, 2003. Retrieved October 1, 2008, at: portal.acm.org/ citation.cfm?id=383768. [10] B. Schneier, The Blow¯sh Encryption Algorithm, Retrieved Oct. 25,
2008. (http://www. schneier.com/blow¯sh.html)
[11] Anjali Patil1, Rajeshwari Goudar2 ―Sensitive Data Storage in Wireless Devices Using AES Algorithm‖ International Journal Of Engineering And Computer Science ISSN:2319-7242Volume 2 Issue 9 September 2013 Page No. 2861-2865.
Author Profile
Sunil Kumar Sahu is M Tech scholar at the Department of Computer Science & engineering, RCET Bhilai (CG).He has passed BE from CSVTU university with HONOURS division.