Undergraduates in computer science and information technology using the internet as a resource
Full text
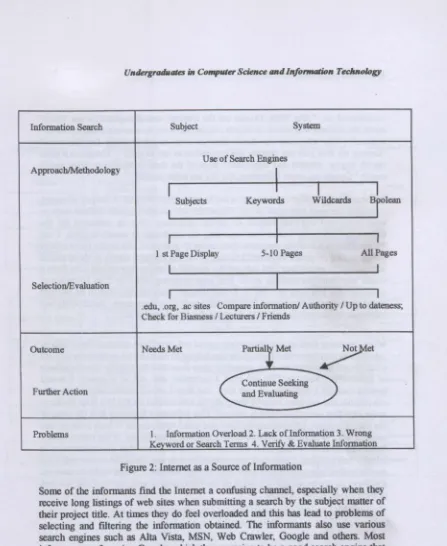
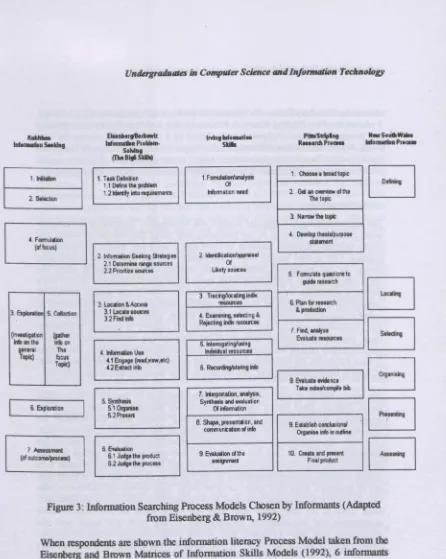
Figure


Related documents
We carry out series of optimizations for wings based on three significantly different aircraft configurations (long-range transport, regional transport, and short-range commuter)
The current framework for protecting users of social media does not work. Modern cybersecurity laws do not apply to the social media model of sharing or
The Policy Editor allows you to submit and assign policies and policy sets to the computers and asset groups in your enterprise.When you start the Policy Editor you connect to
It is based on the random utility model presented in Section 3.1 and uses the estimated type-specific parameters of Session 2 on all dictator and reciprocity games.. The Many Faces
Company is facing increased costs associated with SMS fraud on company-liable mobile service subscriptions.. Anecdotal evidence that increasing amounts of corporate data
86. Define and briefly explain what is meant by each of the following terms. a) strategic vision b) stretch objectives c) strategic objective d) balanced scorecard e)
So we face a big agenda: to ensure that Africa is part of a global stimulus plan, to get immediate and adequate support, including to prevent suffering, and to reform the
Identification of camel milk and shubat microflora provides a theoretical foundation for developing starter cultures by using local LAB strains for industrial production of