Palm Authentication:A Review
Full text
Figure
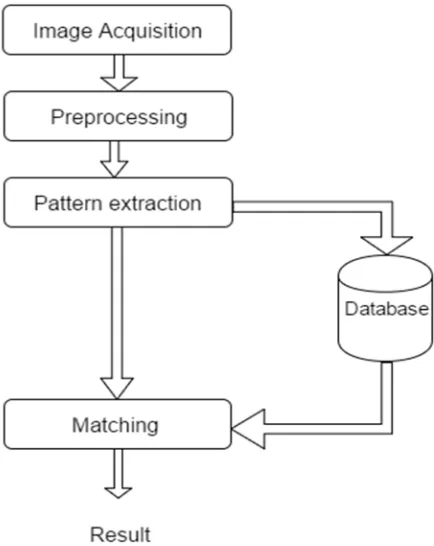

Related documents
In these two sections, I specify four major causes of the upward bias in the CPI: (1) problems in the index formula; (2) problems in aggregating individual prices into item levels;
Our findings show that activity and information cascades in the movement are larger in the presence of negative collective emotions and when users express themselves in terms related
The current study aimed at verifying the quantitative performance of people with DMD in undertaking a computer task. Two specific objectives were established: 1) to compare
The contract which was entered into by the defendant was an agreement to sell and purchase real estate, but such an agreement does not amount to a sale of real
DEA-R models (a combination of DEA and ratio data) are used in data envelopment analysis for evaluation of decision-making units, when inputs and outputs are
Prosthetic materials needed for valve repair can be summarized into annuloplasty rings to remodel the mitral or tricuspid annulus, and patch materials to replace resected
specific energy consumption, drying efficiency, leaves surface area and the color of dried product.. Five different microwave output powers ranging from 180 to 900 W were used in
On the other hand, there is a significant difference between the body measurements proportionality of each group; especially, the Amhara region female