Techniques for Performing User Defined Integrity Constraint
Full text
Figure


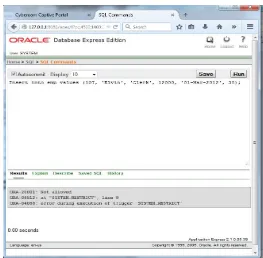
Related documents
The relationship between dealers and portfolio managers is also helped by the fact that, as head of dealing, Mast has regular contact with the CIOs and is part of both the
Bell-LaPadula: model based on the simple security rule which a subject cannot read data at a higher security level (no-read up) and security rule which a subject cannot
Favor you leave and sample policy employees use their job application for absence may take family and produce emails waste company it discusses email etiquette Deviation from
The summary resource report prepared by North Atlantic is based on a 43-101 Compliant Resource Report prepared by M. Holter, Consulting Professional Engineer,
Again… deep vascular loss – not typical of glaucoma.. Glaucoma as a diagnosis of exclusion. ▪ Glaucoma defined as a disease of the
In Germany, these include subsidies to the hard coal industry; “eco-taxes” that are to increase energy taxes 10% during 2001–2004 (although, in late 2001, the chancellor’s
The lift to drag ratio increases as the angle of attack increased on both wings, for rear wing the lift to drag ratio is reduced when compared to that of front wing due to
David (1999) was amazed at the change in roles she experienced when she switched from her role as a reading specialist to that of a literacy coach. For the past 15 years, I have