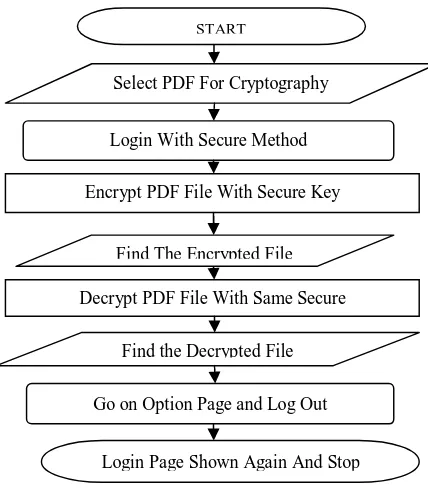
Data Security by Encryption Decryption using AES Algorithm of Cryptography
Full text
Figure


Related documents
The readable message (original) is called plaintext.The secret message (not readable) is called cipher text.The process of converting plaintext to ciphertext is called
CUAJ ? January February 2016 ? Volume 10, Issues 1 2 ? 2016 Canadian Urological Association E1 ORIGINAL RESEARCH Cite as Can Urol Assoc J 2016;10(1 2) E1 6 http //dx doi org/10 5489/cuaj
We extracted the following information from each included study: (1) author, (2) title, (3) publication year, (4) geographical location, (5) study design, (6) sample size, (7) age
The MCGT [3], CET [23], and GTSA [22] techniques incorrectly segment some low-intensity areas (e.g., cell nuclei) in the dermis area as the epidermis area, which increases the
PASCUAL-LEONE beschrieb 1994 anhand der Untersuchung vier verschiedener Handmuskeln an 9 Probanden, dass die größten Amplitudenausschläge über der linken Hemisphäre bei
Table 4 showed that, heart girth was higher in animals supplemented with groundnut cake and Seyal pods compared with those on natural grazing, ewe lambs supplemented with
The percentage of subjects consuming alcohol remained same in day workers but in shift workers it increased to 61.7 per cent after taking up the job and the quantity of
As the heat flux increases, the outlet temperature goes on increasing because the fluid gets heated up more and more due to convective heat transfer which is evident from