Robust Distant Supervision Relation Extraction via Deep Reinforcement Learning
Full text
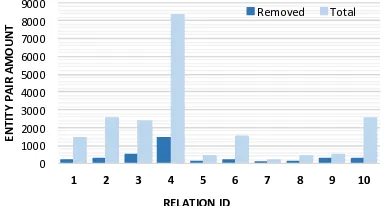
Figure
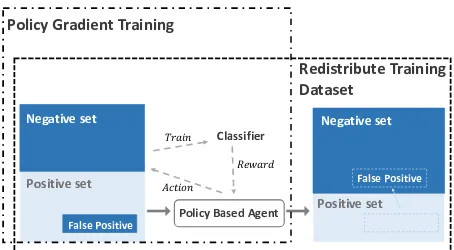


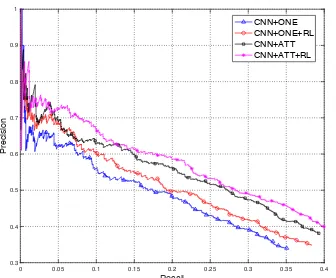
Related documents
The typical observations of the strength of the returns address the behavior during quasi-equilibrium conditions; that is, the changes in the solar illumination and thus the
It is in this context that this study examines the impact of fiscal policy on output, consumption, investment and foreign trade using a dynamic stochastic general equilibrium DSGE
Spring 2016 Catalog Addendum 36 CSUSM The Core (17 units) – Certificate of Advanced Study in Core Business Knowledge.. The Core is a multi-disciplinary graduate 600-level set
This research was aimed at developing the use of journals can develop the ability of the eleventh grade students at SMA Negeri 1 Sojol in writing Recount text. It was
The purpose of this interview is to get your view regarding the reasons that result to non – compliance state of compliance with the conditions of employment in this company and
Our research suggests that a better understanding of the four catalysts identified (family, roles, loss, spaces and places) and older people’s digital trajectories will
During analysis of threats associated with integration of a new technology like the iPhone, the team uncovered default settings in our Microsoft Exchange ActiveSync environment
The ESUKOM approach fo- cuses on the integration of available and widely deployed security measures (both commercial and open source) based upon the Trusted Computing Group’s