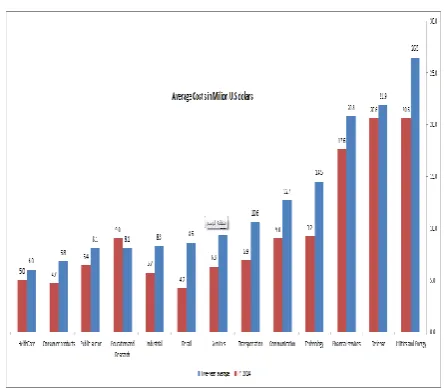
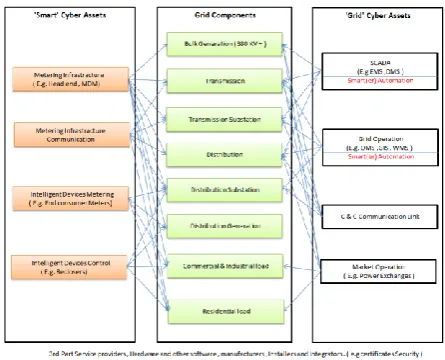
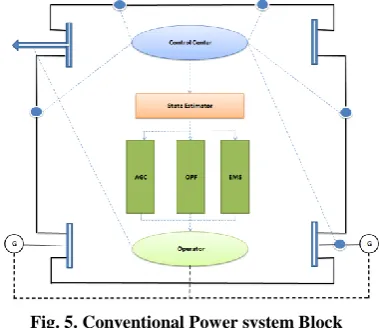
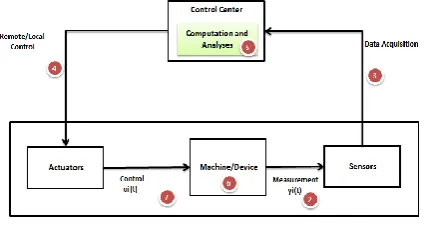
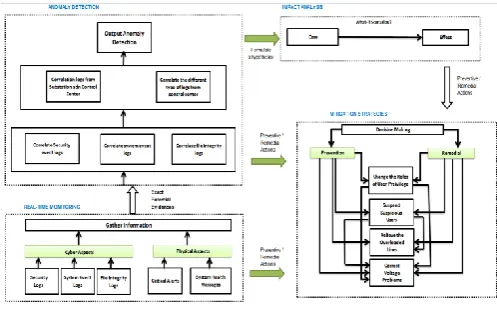
Vulnerability and Forensics associated with the Smart Grid: Cyber Attacks
Full text
Figure
Related documents
For FY 2022-23 and future years, these costs will be paid by the Department of Public Safety with Highway Users Tax Fund (HUTF) and General Fund money through common
The incentives for workers to acquire skills relevant for the private sector will remain low, existing labor market deficiencies are likely to be exacerbated, and the skill gap
Nigel has in-depth knowledge of cyber security, information security, business risk, data breach incident response, digital forensics, business continuity, cyber warfare, cyber
One advantage of switching to charge on administration is that medications dispensed but refused or not given to the patient for other reasons are not charged to the
PLS-SEM analysis, it can be concluded that both website design quality (t-value = 2.714) and service quality (t-value = 3.190) have a positive effect on repurchase inten-
Based on our experience with Regulation Room, an experimental online participation platform trying to broaden meaningful public engagement in the process federal agencies
The current study com- pared the cross-sectional data and found that countries with higher national income have lower mortality rate and developed economy can help to reduce
We do this by analysing the pricing behaviour of petrol stations along the station density in different city districts in Germany, where a district is an administrative unit at