Security awareness: A lesson from Tcpdump and Ethereal
Full text
Figure

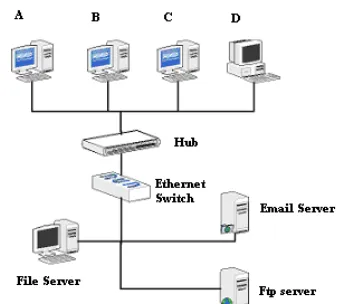

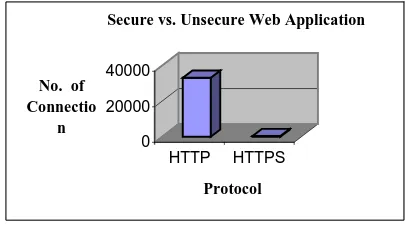
Related documents
one of the following: white British, white Irish, white other, black Caribbean, black African, black other, black Caribbean and white, black African and white, Indian,
Note: if this is you first time making a request through CommunityUse, you will be asked to read the terms and conditions that the district provides.. You will also be asked to
This guide contains information on using the IBM Client Security Password Manager program to manage and recall your sensitive login information.. This guide is organized
For example, if FileMaker Server is hosting files, an intruder could access data if the files lack sufficient user account security. An intruder who knows how a WAN controls
MGT of America performed an annual inspection for compliance with the ICE National Detention Standards (NOS) at the Central Texas Detention Facility (CTDF) located in San
There a lot of studies concerning the price linkage and asymmetric price transmission between the same commodities in the foreign and domestic market (see Meyer and
• Inadequate user information security awareness of sensitive data handling. Vulnerabilities