Jackpot Stealing Information From Large Caches via Huge Pages
Full text
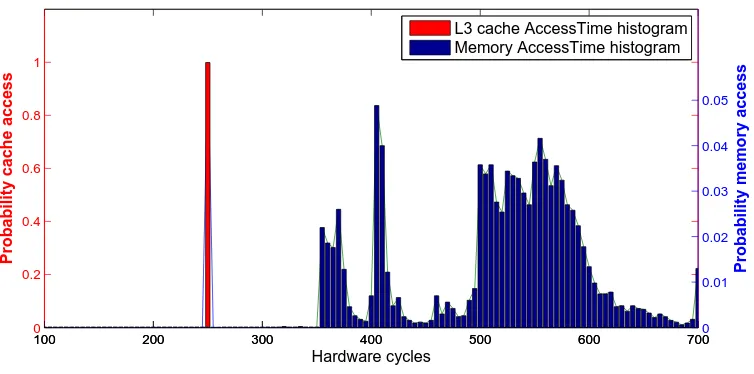
Figure



Related documents
In Germany, these include subsidies to the hard coal industry; “eco-taxes” that are to increase energy taxes 10% during 2001–2004 (although, in late 2001, the chancellor’s
On June 9, 2003, the Tax Discovery Bureau (Bureau) of the Idaho State Tax Commission issued a Notice of Deficiency Determination (NODD) to [Redacted] (taxpayers), proposing income
Favor you leave and sample policy employees use their job application for absence may take family and produce emails waste company it discusses email etiquette Deviation from
153 TABLE 5.3: PROPORTIONS AND THEIR 95% CONFIDENCE INTERVAL OF RESPONDENTS WHO APPLIED DIFFERENT PROTECTIVE WILDLIFE FOOD HANDLING BEHAVIORS IN INUKJUAK, NUNAVIK, CANADA .... 154
The property is located on the east side of School Street between North Lane and Highland Road in the City of Glen Cove and is on the public sewer system.. The Glen Street Long
At the risk of over-simplifying, inflation targeting central banks in the industrial world are by far the most reluctant to wield this instrument while monetary authorities in
Step 5 is used to check the cable length by introducing a short between the data lines on the first connector and measuring the loop resistance at the last connector.. • Step


