Privacy Preserving Enforcement of Sensitive Policies in Outsourced and Distributed Environments
Full text
Figure


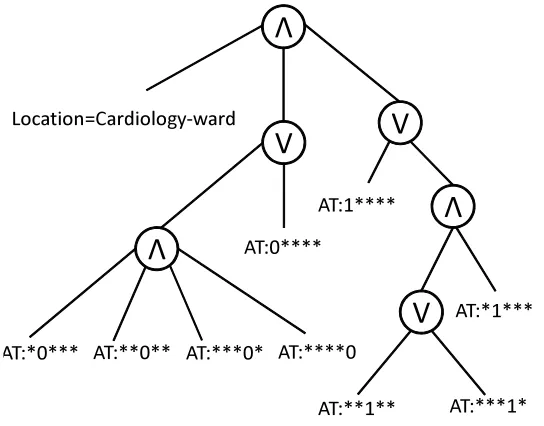

Outline
Related documents
At the time of this writing there are two publicly available implementations of this interface: one is based on the JDK XPath [5] and another is based on the "Virtual
• Straightforward… transect the gastric tube, 5-6 cm distal to the GE junction to create gastric pouch. • Things to keep
Body size dimorphism between immature and early sexually recruited cohorts of farmed Scottish Atlantic salmon was investigated with the view to optimizing the
Sea water can also be used in a RAS land farm, and the produced fish could reach higher weights (e.g. However the economically optimal size for transfer is not known. By using
Policy: Asset Management Policies: Data Protection & Privacy Access Control Policies: Information System Acquisition, Development, Maintenance
Working with the Navy Pier team, ABM implemented dynamic pricing to maximize revenue, automated the debit card process to save time, and introduced online parking reservations
Step 4 For each VM, edit the domain XML descriptor file (and any network XML files, if present) to configure a vNIC interface that is directly attached to the VIC and uses the
the City’s camera privacy policies. However, the City’s contracts regarding access to private cameras do not specifically provide that the City’s camera privacy poli- cies govern





