A Security Design for Cloud Computing: An Implementation of an On Premises Authentication with Kerberos and IPSec within a Network
Full text
Figure
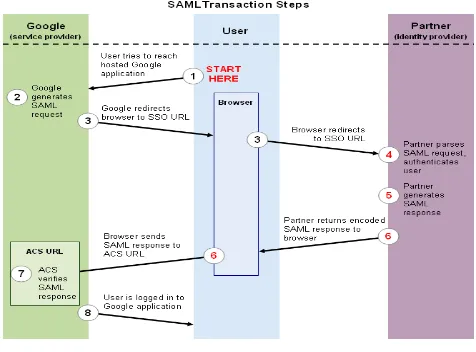
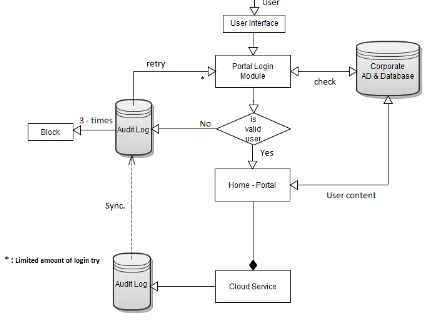
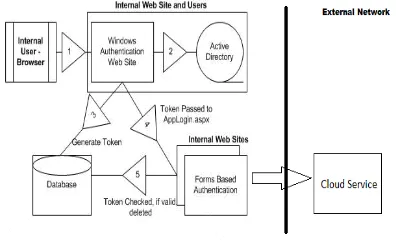
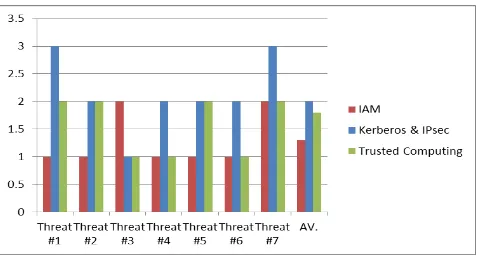
Related documents
A bank that allows for remote opening is often located in a country that does not offer western-style comforts like deposit insurance, and is typically a “traditional offshore”
The Regions tab enables you to create delivery regions containing the weight based delivery cost levels and postcode information that will be used to calculate delivery costs
Due to lack of data on mortality impact caused by NTDs in the State of Sergipe, Northeast Region of Brazil, the present paper provides information concern- ing these neglected
Ques esti tion on Nu Numb mber er.. ! ! pu pure re ca capa paci cito tor2 r2 in indu duct ctor or an and r d res esis isto tor a r are re co conn nnec ecte ted i d in s n ser
Up and over door locks with 5 pins (2 picking resistant) round cylinder Up and over door locks either with europrofile cylinder 5 pins (2 picking resistant) or with high security 6
• Money matters pervade client affairs • FS demands regular client contact • IFAs can share client factfind data • Can assist with client segmentation • Provide the basis
The structural-level discussion of the relative workplace and household power of husbands and wives is relevant to the gender gap in delinquency because it influences the
Results: The results showed a significant difference between students with type D personality and non-type D personality in regard to general health, and in regard to