International Journal of Scientific Research in Computer Science, Engineering and Information Technology © 2018 IJSRCSEIT | Volume 3 | Issue 1 | ISSN : 2456-3307
EnDAS. Efficient Encrypted Data Search as a Mobile Cloud
Service
CH. Haritha1, P. Praveen Kumar2
1M.Tech Scholar, Department of CSE, Vignana Bharathi Institute of Technology Aushapur (V), Ghatkesar (M), R.R, Telangana, India
2Assistant Professor, Department of CSE, Vignana Bharathi Institute of Technology Aushapur (V), Ghatkesar (M), R.R., Telangana, India
ABSTRACT
Record amassing in the cloud system is rapidly grabbing notoriety all through the world. In any case, it stances peril to buyers unless the data is encoded for security. Mixed data should be sufficiently open and retrievable with no security spills, particularly for the flexible client. Yet late research has handled various security issues, the plan can't be associated on phones particularly under the convenient cloud condition. This is an immediate aftereffect of the inconveniences obliged by remote structures, for example, inertia affectability, poor openness, and low transmission rates. This prompts a long intrigue time and additional system activity costs while utilizing standard demand outlines. This examination keeps an eye on these issues by proposing a viable Encrypted Data Search (EnDAS) scheme as an adaptable cloud advantage. This inventive arrangement uses a lightweight trapdoor (encoded catchphrase) weight strategy, which propels the data correspondence process by diminishing the trapdoor's size for action capability. In this examination, we in like manner propose two streamlining procedures for report look for, called the Trapdoor Mapping Table (TMT) module and Ranked Serial Binary Search (RSBS) count, to speed the interest time. Results show that EnDAS diminishes look time by and also orchestrate development.
Keywords :Encrypted Data Search, Trapdoor Mapping Table, Mobile Cloud Service, Cloud Server
I.
INTRODUCTION
SINCE circulated registering can reinforce adaptable organizations and give a preservationist use of limit and computation resources, it is rapidly getting unmistakable quality. With successful cloud organizations, various data providers can populate their data in fogs as opposed to explicitly serving customers. The cloud also empowers providers to assign basic errands, for instance, record looks. To guarantee data security, the records and their documents are for the most part encoded before outsourcing to the cloud for seeks. At the point when customers need to request certain reports, they at first send catchphrases to the main data provider.
security ensuring interest systems Mobile devices (e.g. PDAs and tablets) were surveyed to beat two billion advancement (0.3 billion for PCs) in the year 2014, which overpowers the general shipment of purchaser equipment devices. Nowadays, customers seriously utilize mobile phones to request report look organizations.
II.
LITERATURE SURVEY
Algorithms.
Fah Algorithm. Fast Accumulated Hashing
Another no trapdoor gatherer for total hashing is exhibited. It can be successfully recognized before long using existing cryptographic hash figurings and pseudorandom progression generators. The memory essential isn't precisely in identical check based plans.
Rss Algorithm. Ranked Serial Search
Cryptographic. (a procedure called encryption), Cryptography is a technique for putting away and transmitting information in a specific shape with the goal that those for whom it is proposed can read and process it.
Cryptography is a system for securing and transmitting data in a particular shape with the objective that those for whom it is proposed can read and process it.
ciphertext is then back again (known as unraveling). Individuals who sharpen this field are known as cryptographers.
Rsbs Algorithm. Ranked Serial Binary Search LSB. Last significant bit
III.
EXISTING SYSTEM
Here the FAH encryption figuring for record documents is used in past composing. Utilizing this FAH computation, we encode cuts of each rundown. Low down encryption process for one cut Slice of the record IC is that encoding l-bit term t in Slice is used by the hash work , and mapping l-bit mixed term into r-bit overhauled term is by the mapping limit, where and after that conglomerating all the r-bit streamlined terms together. Finally we get the mixed cut Slice. Along these lines, we can scramble the rundown IC by gathering each one of the cuts (s cuts), and get the encoded list IC makes back the initial investment with amassing all the streamlined terms in this file.
IV.
PROPOSED SYSTEM
1. The situated watchword chase will return records to the criticalness score. Zero et al. proposed a novel framework that impacts the server to side do the chase operation. Regardless, it should send various immaterial reports back and let the customer channel them. This is an abuse of development, which is unsatisfactory for the versatile cloud. Arbors et al.
2. Proposed a spread cryptographic structure that ensured the security of the report recuperation process and the high availability of the system,
however this structure encounters two
frameworks round treks and estimation
flightiness for target reports. Wang et al. proposed a singular round trek mixed request contrive, however their structure isn't adequately secure, as it discharges the catchphrase and
related report information from various
V.
SYSTEM DESIGN
Figure 1. System Architecture
Figure 2. Data Flow Diagram (USER)
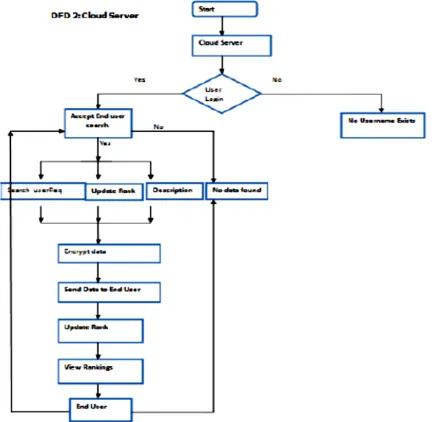
Figure 3. Data Flow Diagram (CLOUD SERVER)
VI.
IMPLEMENTATION
Module Description 1. Data User Module
This module incorporates the client enlistment login subtle elements.
2. Data Owner Module
This module causes the proprietor to enroll those points of interest and furthermore incorporate login subtle elements
3. File Upload Module
This module helps the proprietor to transfer his record with encryption utilizing RSA algorithm. This guarantees the documents to be shielded from unapproved client.
4. Rank Search Module
This module guarantees the client to look through the document that is sought regularly utilizing rank inquiry.
5. File Download Module
This module enables the client to download the document utilizing his mystery key to decode the downloaded information.
6. View Uploaded and Downloaded File
This module enables the Owner to see the transferred documents and downloaded records.
VII.
SYSTEM TESTING
VIII.
INPUT DESIGN AND OUTPUT DESIGN
Input Design
The data arrangement is the association between the information system and the customer. It contains the making point of interest and techniques for data course of action and those methods are vital to put trade data in to a usable shape for planning can be refined by surveying the PC to examine data from a made or printed report or it can occur by having people entering the data direct into the system. The arrangement of data focuses on controlling the measure of data required, controlling the botches, keeping up a key separation from delay, avoiding extra means and keeping the strategy clear. The data is laid out in such a course thusly, to the point that it gives security and convenience with holding the assurance. Data Design considered the going with things.
1. What information ought to be given as info? 2. How the information ought to be orchestrated or
coded?
3. The exchange to control the working staff in giving information.
4. Methods for getting ready information approvals and ventures to take after when mistake happen.
Output Design
A quality yield is one, which meets the essentials of the end customer and presents the information clearly. In any system outcomes of taking care of are conferred to the customers and to other structure through yields. In yield design it is settled how the information is to be unstuck for snappy need and moreover the printed duplicate yield. It is the most basic and direct source information to the customer. Capable and astute yield setup upgrades the system's relationship to help customer fundamental authority. 1. Arranging PC yield should proceed in a dealt with, well altogether considered way; the right yield must be created while ensuring that each yield segment is made with the objective that people will find the structure can use easily and satisfactorily. Exactly when examination plot PC yield, they ought to recognize the specific yield that is required to meet the essentials.
2. Select systems for presenting information. 3. Influence record, to report, or diverse plans that
contain information made by the system.
IX.
RESULTS
Figure 3. Cloud Server Login Figure 4. Cloud Server Main
Figure 5. Give Privileges Figure 6. Cloud Server Files
Figure 7. File Contents Figure 8. Attackers
Figure 11. Data Owners Figure 12. User Registration
Figure 13. Owner Registration Figure 14. Upload Data
Figure 15. Search Result Figure 16. Request for Trapdoor & Secret Key
X.
CONCLUSION
In this work, we proposed a novel encoded look framework EnDAS over the adaptable cloud, which enhances make improvement and intrigue time productivity separated and the standard structure. We began with a genuine examination of the standard encoded look structure and inquired about its bottlenecks in the versatile cloud: create advancement and intrigue time wastefulness. By then we developed a beneficial outline of EnDAS which is sensible for the compact cloud to address these issues, where we utilized the TMT module and the RSBS computation to adjust to the inefficient request time issue, while a trapdoor weight procedure was used to decrease compose movement costs. Finally our evaluation looks at likely shows the execution inclinations of EnDAS.
XI.
REFERENCES
[1].D. Huang, "Mobile cloud computing," IEEE
COMSOC Multimedia Commun. Tech.
Committee (MMTC) E-Letter, vol. 6, no. 10, pp. secure and efficient ranked keyword search over outsourced cloud data," IEEE Trans. Parallel Distrib. Systems, vol. 23, no. 8, pp. 1467-1479, 2012.
[4].C. Wang, N. Cao, J. Li, K. Ren, and W. Lou, "Secure ranked keyword search over encrypted cloud data," in Proc. IEEE Int. Conf. Distrib. Comput. Syst. (ICDCS), Jun. 2010, pp. 253-262. [5].C. Gentry and S. Halevi, "Implementing gentrys
fullyhomomorphic encryption scheme," in Advances in Cryptology- EUROCRYPT 2011, 2011, pp. 129-148.